Applies to: Exchange Server 2007 SP3, Exchange Server
2007 SP2, Exchange Server 2007 SP1, Exchange Server 2007
Topic Last Modified: 2009-01-22
When an external user sends e-mail messages to a Microsoft Exchange server that runs the anti-spam features, the anti-spam features cumulatively evaluate characteristics of inbound messages and either filter out messages that are suspected to be spam or assign messages a rating based on the probability that the message is spam. This rating is stored with the message as a message property that is called the spam confidence level (SCL) rating. This rating is persisted with the message when the message is sent to other Exchange servers.
Figure 1 shows the order in which the default anti-spam features and Microsoft Forefront Security for Exchange Server filter inbound messages from the Internet. By default, the anti-spam and antivirus features are arranged in this order with the filters that use the least resources filtering first, and then the filters with that use the greatest resources filtering last.
 Note: Note: |
|---|
| Additional anti-spam features may become available in the future. As new anti-spam features are developed, they will be included in the overall mail flow. Additionally, the following figure and explanation assume that the Exchange Server 2007 Edge Transport server is the first Simple Mail Transfer Protocol (SMTP) server to accept inbound messages. In some organizations, the Edge Transport server may be deployed behind a third-party SMTP server. When the Exchange 2007 Edge Transport server is deployed behind a third-party SMTP gateway server, the Exchange 2007 Edge Transport server requires additional configuration. Specifically, you must make sure that all SMTP gateway servers are listed in the InternalSMTPServer property of the TransportConfig object. For more information, see Set-TransportConfig. |
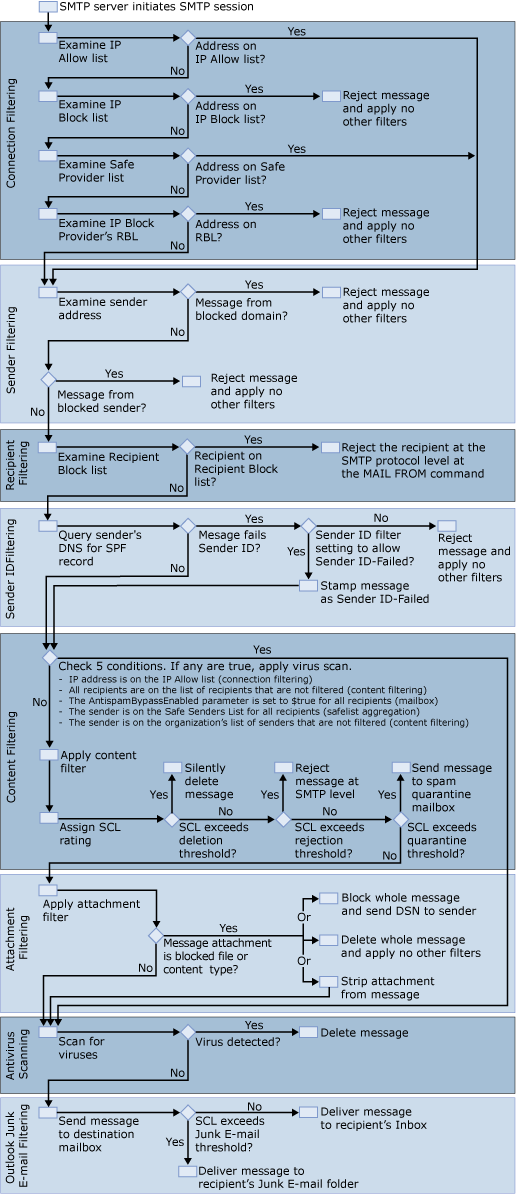
As shown in Figure 1, filters are applied in the following order when the Edge Transport server is Internet-facing:
- A SMTP server connects to Exchange 2007 and initiates an
SMTP session.
- Connection filtering
- Sender filtering
- Recipient filtering
- Sender ID filtering
- Content filtering
- Attachment filtering
- Antivirus scanning
 Note: Note: |
|---|
| Although this detail is not shown in Figure 1, connection filtering gathers information during two different events. The first event where connection filtering gathers information is shown in Figure 1, where connection filtering gathers IP address information from the connection. The second time connection filtering gathers information is shown in Figure 3 when the Sender Filter agent parses the message headers to determine the first external IP address. Agents may monitor multiple events. Figure 1 shows a high-level view of the rough order that agents are applied, when all agents are enabled, for the purposes of illustrating message flow. For more information about specific events and which agents monitor which events, see Overview of Transport Agents. |
 Connection Filtering
Connection Filtering
During the SMTP session, Exchange 2007 applies connection filtering by using the following criteria as shown in Figure 2.
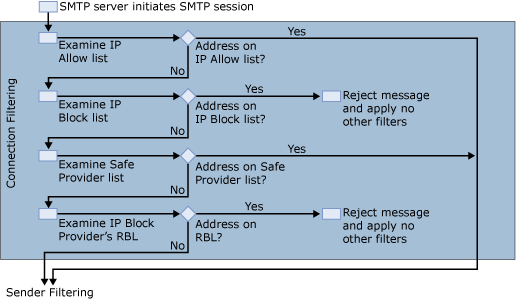
- The Connection filter agent examines the administrator-defined
IP Allow list. If the IP address of the sending server is on the
administrator-defined IP Allow list, the message is then process by
Sender Filtering.
- The Connection filter agent examines the local IP Block list.
If the IP address of the sending server is found on the local IP
Block list, the message is automatically rejected, and no other
filters are applied.
- The Connection filter agent examines the list of allowed IP
addresses that any IP Allow List providers that you have. If the IP
address of the sending server is on the list of allowed IP
addresses from IP Allow List providers, the message is then
processed by Sender Filtering.
- The Connection filter agent examines the real-time block lists
(RBL) of any IP Block List providers that you have configured. If
the sending server's IP address is found on a RBL, the message is
rejected, and no other filters are applied.
For more information, see Configuring Connection Filtering.
 Note: Note: |
|---|
| If the Connection filter agent is deployed on a computer that is behind another server that faces the Internet, other filters, such as sender filtering and recipient filtering, are invoked before the Connection Filter agent. |
 Sender Filtering
Sender Filtering
After connection filtering has been applied, Exchange 2007 examines the sender e-mail address against the list of blocked senders that you configure in sender filtering as shown in Figure 3.
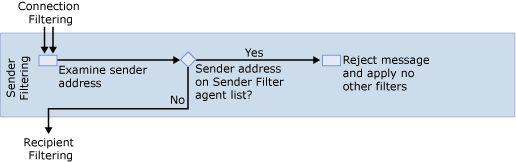
The Sender Filter agent then checks the sender's e-mail address that is contained in the From: header fields in the message envelope and the message header. If either From: header field matches the address in the Blocked Sender list, Exchange 2007 rejects the message at the protocol level, and no other filters are applied.
 Note: Note: |
|---|
| Even if recipients in your organization have put senders on their Microsoft Office Outlook Safe Senders List, sender filtering on the Edge Transport server will override the recipient's Outlook setting and reject the messages. |
For more information about sender filtering, see Configuring Sender Filtering.
For more information about message envelopes and message headers, see Managing the Replay Directory.
 Recipient Filtering
Recipient Filtering
If sender filtering does not reject the message, Exchange runs connection filtering again. Exchange then applies the Recipient Filter agent as shown in Figure 4.
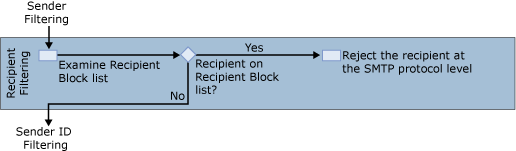
The Recipient Filter agent examines the recipient against the Recipient Block list that you configure in the recipient filter agent settings. If the intended recipient matches an e-mail address on your Recipient Block list, Exchange 2007 rejects the message for that particular recipient. In addition, the Recipient Filter agent checks to see whether the recipient is present in the organization. If the recipient is not present in the organization, Exchange rejects the message for that particular recipient.
If multiple recipients are listed on the message and all the recipients are not on the Recipient Block list, the message will continue to process. Otherwise, if the message is bound for only a single blocked recipient, no other filters are applied.
When a message with blocked recipients is processed, the set of blocked recipients are removed from the message, and the message continues into the organization. Protocol-level SMTP rejection responses are sent to the sender for each blocked recipient. The Sender Reputation agent monitors the OnReject event to calculate sender reputation level.
For more information, see Configuring Recipient Filtering.
 Sender ID Filtering
Sender ID Filtering
If the message still contains valid recipients after recipient filtering has been applied, Exchange 2007 runs Sender ID as shown in Figure 5.
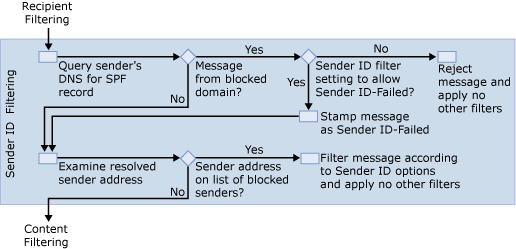
First, the Sender ID agent determines the Purported Responsible Address (PRA) of the message using the algorithm described in RFC 4407. This step is required to accurately identify the message's sender. The PRA is an SMTP address, such as kim@contoso.com. The Sender ID agent then performs a domain name service (DNS) lookup against the domain part of the PRA. If that domain has published a sender policy framework (SPF) record, the agent uses the SPF record to evaluate the message according to the specification for RFC 4408. The result of the evaluation is stamped on the message in the anti-spam stamp. If that domain does not have a published SPF record, the Sender ID agent stamps a Sender ID result of "None" on the message. For more information about the types of stamps used for Sender ID filtering, see Anti-Spam Stamps.
If the sender's DNS is from a blocked domain or a blocked address, the following actions may be taken depending on your configuration of Sender ID actions:
- Reject message If the Sender ID action
is set to Reject Message, Exchange rejects the message and
sends an SMTP error response to the sending server. The SMTP error
response is a 5xx level protocol response with text that
corresponds to the Sender ID status.
- Delete message If the Sender ID action
is set to Delete Message, Exchange deletes the message
without informing the sending server of the deletion. In fact, the
computer that has the Edge Transport server role installed sends a
fake "OK" SMTP command to the sending server and then deletes the
message. Because the sending server assumes that the message was
sent, the sending server will not retry sending the message in the
same session.
- Stamp message with Sender ID result and continue
processing Exchange stamps the message with
the Sender ID result and continues processing the message. This
metadata is evaluated by the Content Filter agent when a SCL is
calculated. Additionally, sender reputation uses the message
metadata when it calculates a sender reputation level for the
sender of the message.
For more information, see Configuring Sender ID.
 Content Filtering
Content Filtering
Before Exchange content filtering calls the Exchange Intelligent Message Filter, it applies sender filtering again. The Exchange server then applies the Content Filter agent as shown in Figure 6.
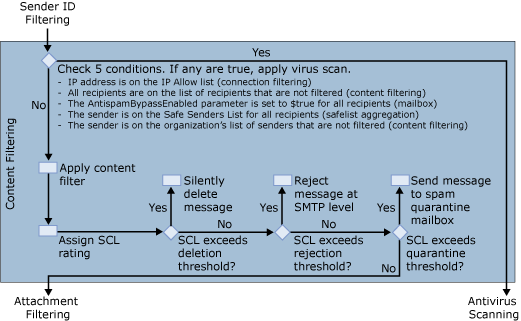
The Content Filter agent checks the following conditions in the message. If any of the conditions are true, the message bypasses content filtering. These messages then go on to antivirus scanning for processing.
- The sender's IP address is on the IP Allow list for connection
filtering.
- All recipients are on the exceptions list for content
filtering.
- The AntiSpamBypassEnabled parameter is set to
$Trueon all the recipients' mailboxes.
- All the recipients have added this sender to their Outlook Safe
Sender list, which is updated to the Edge Transport server by
using safelist aggregation.
- The sender is a trusted partner and on the organization's list
of senders that are not filtered.
In addition to the conditions listed here, if the SMTP session has been authenticated as a trusted partner, and if the administrator has granted the Bypass Anti-Spam (Ms-Exch-Bypass-Anti-Spam) permission to partners, the anti-spam agents will be disabled for messages during that session. The Bypass Anti-Spam permission is not granted to partners by default and must be assigned by an administrator.
If a message does not meet any of the conditions described here, content filtering is applied. Content filtering assigns a SCL rating to the message. Based on the SCL rating, one of the following actions occurs:
- If the SCL rating on the message is equal to or greater than
the SCL delete threshold and the SCL delete threshold is enabled,
the Content Filter agent deletes the message. There is no
protocol-level communication that tells the sending system or
sender that the message was deleted. If the SCL rating is lower
than the SCL delete threshold value, the Content Filter agent does
not delete the message. Instead, the Content Filter agent compares
the SCL value to the SCL reject threshold.
- If the SCL rating on the message is equal to or greater than
the SCL reject threshold and the SCL reject threshold is enabled,
the Content Filter agent rejects the message and sends a rejection
response to the sending system. You can customize the rejection
response. In some cases, a non-delivery report (NDR) is sent to the
original sender of the message. If the SCL rating is lower than the
SCL reject threshold value, the Content Filter agent does not
reject the message. Instead, the Content Filter agent compares the
SCL value to the SCL quarantine threshold.
- If the SCL rating on the message is equal to or greater than
the SCL quarantine threshold and the SCL quarantine threshold is
enabled, the Content Filter agent sends the message to the spam
quarantine mailbox. For more information about how to manage the
spam quarantine, see Configuring and Managing
Spam Quarantine. The message then continues to attachment
filtering.
For more information, see the following topics:
 Attachment Filtering
Attachment Filtering
After content filtering has been applied, Exchange applies attachment filtering as shown in Figure 7.
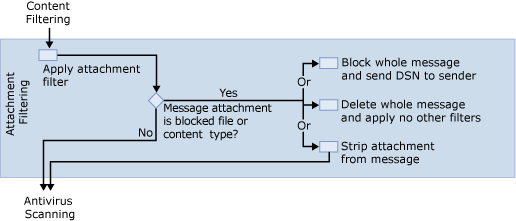
You can configure attachment filtering to block attachments based on their MIME content type, file name, or file name extension. If attachment filtering detects a content type of file name that has been blocked, one of the following actions will occur based on your attachment filtering settings:
- Reject If action setting is set to
Reject, both the e-mail message and attachment are prevented from
being delivered to the recipient and the system generates a DSN
failure message to the sender. You can customize your rejection
response.
- Silent Delete If the action setting is
set to Silent Delete, both the e-mail message and attachment are
prevented from being delivered to the recipient. A notification
that the e-mail message and attachment were blocked is not returned
to the sender.
- Strip If the action setting is set to
Strip, the attachment is stripped from the e-mail message. This
value allows the message and other attachments that do not match an
entry on the attachment block list to be delivered to the
recipient. A notification that the attachment was blocked is added
to the recipient's e-mail message.
If the message was not rejected or deleted, or attachment filtering did not detect blocked attachment types, the message is then scanned for viruses.
For more information, see How to Configure Attachment Filtering.
 Antivirus Scanning
Antivirus Scanning
After attachment filtering has been applied, or if the recipients were bypassed in content filtering, Forefront Security for Exchange Server antivirus scanning is applied as shown in Figure 8.
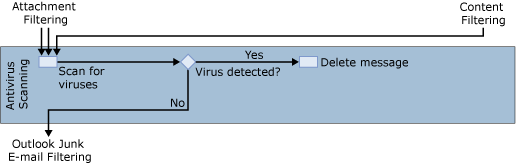
Forefront Security for Exchange Server is an antivirus software package that is tightly integrated with Exchange 2007 and offers additional antivirus protection for your Exchange environment. When Forefront Security for Exchange Server detects messages that seem to contain a virus, the system deletes the message, generates a notification message, and sends the notification to the recipient’s mailbox.
For more information about Forefront Security for Exchange Server, see Protecting Your Microsoft Exchange Organization with Microsoft Forefront Security for Exchange Server.
 Outlook Junk E-mail
Filtering
Outlook Junk E-mail
Filtering
After all the filters are applied and the message has been scanned for viruses, the message is sent to the intended recipient's mailbox and the Junk E-mail filtering is applied as shown in Figure 9.
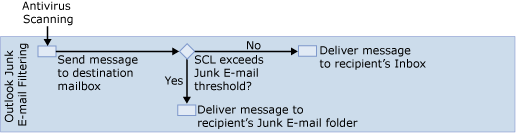
If the SCL rating for the message is equal to or greater than the SCL Junk E-mail folder threshold and the SCL Junk E-mail folder threshold is enabled, the Mailbox server puts the message in the Outlook user's Junk E-mail folder. If the SCL value for a message is lower than the values for the SCL delete, reject, quarantine, and Junk E-mail folder thresholds, the Mailbox server puts the message in the user's Inbox. For more information about the SCL thresholds, see Adjusting the Spam Confidence Level Threshold.
 For More Information
For More Information
For more information about anti-spam and antivirus features, see the following topics:

