Topic Last Modified: 2011-05-02
Federation provides your organization with the ability to communicate with other organizations’ Access Edge Servers to share IM and presence. If you have enabled federation on the Access Edge service, access by federated partners is controlled using one of the following methods:
- Allow automatic discovery of federated partners. This is
the default option during the initial configuration of an Access
Edge service because it balances security with ease of
configuration and management. For example, when you enable
automatic discovery of federated partners on your Access Edge
service, Microsoft Lync Server 2010 allows any federated domain to
send communications with you and automatically evaluates incoming
traffic from federation partners and limits or blocks that traffic
based on the trust level, amount of traffic, and administrator
settings.
- Allow discovery of federated partners, but grant a higher
level of trust to specific domains or Access Edge Servers that you
specify on the Allow list. For example, if you want to grant a
higher level of trust to partners using the SIP domain contoso.com
and fabrikam.com, add these two domains on the Allow tab.
Restricting discovery in this way establishes a higher level of
trust for connections with the domains or Access Edge service that
you add to your Allow list, but it still provides the ease
of management that is possible by discovering other federation
partners that are not listed on the Allow tab. A Block
Domain option is also available to allow filtering of SIP
domains.
- Do not allow discovery of federation partners and limit
access of federated partners to only the domains or Access Edge
Servers for which you want to enable connections. Connections
with federated partners are allowed only with the specific domains
or Access Edge services you add to the Allow tab. This
method offers the highest level of security, but it does not offer
ease of management. For example, if an FQDN of an Access Edge
service changes, you must manually change the FQDN of the server in
the Allow list.
 How Federated Traffic Is
Evaluated When Using Automatic Discovery
How Federated Traffic Is
Evaluated When Using Automatic Discovery
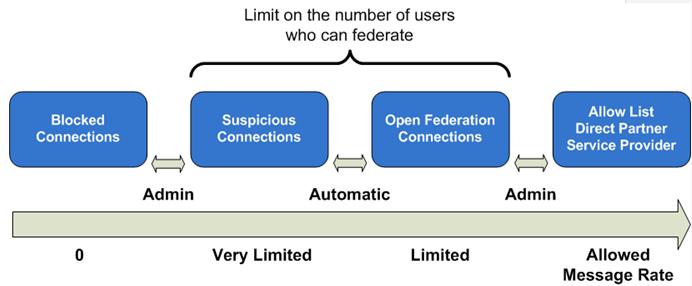
If you choose to use automatic discovery of federated partners, the Access Edge service automatically evaluates incoming federated traffic in the following way:
- If a federated party sends requests to more than 1,000 URIs
(valid or invalid) in the local domain, the connection first placed
on the Watch list is evaluated first. Any additional requests are
blocked by the Access Edge service. If the Access Edge service
detects suspicious traffic on a connection, it limits the
federation partner to a low message rate of one message per second.
The Access Edge service detects suspicious traffic by calculating
the ratio of the number of successful responses to the number of
failed responses. The Access Edge service also limits legitimate
federated partner connections (unless added to the Allow
list) to 20 messages per second. The list of suspicious peer
connects is displayed in the Access Edge service Computer
Management console.
- If you know that you will have more than 1,000 requests sent by
a legitimate federated partner or a volume of more than 20 messages
per second sent to your organization, you must add the federated
partner to the Allow tab to allow these volumes.
The following figure shows rate limitations on open federation.
After configuring federation, you can use the Lync Server administrative tools to manage federated partner access on an ongoing basis. For more information, see the Lync Server Control Panel documentation.

