This section describes what components are required to enable external user access in an Office Communications Server deployment.
 Feature Components
Feature Components
The primary component for enabling external user access is the Edge Server, which is a server role in Office Communications Server. To deploy an Edge Server, run the Office Communications Server deployment tool on a server, choosing the role of Edge Server during setup. Depending on your scaling needs, you install one or more Edge Servers in your deployment.
An Edge Server always runs the following three services:
-
Access Edge service, which provides the core functionality
for collaboration between your internal users and external users.
The Access Edge service provides a single, trusted connection point
for both outbound and inbound Session Initiation Protocol (SIP)
traffic.
-
Web Conferencing Edge service, which enables external users
to join on-premises meetings. This service enables your users to
invite external users to meetings; these external users can include
your organization’s remote users, federated users, and any other
external users who are sent invitations to specific meetings.
-
A/V Edge service, which makes it possible to share audio and
video with external users. Your users can add audio and video to
meetings that include external participants, and they can share
audio and video directly with an external user in point-to-point
sessions. The A/V Edge service also enables your users to use the
Desktop Sharing feature to collaborate with external users.
The following components are also required or recommended to enable external user access.
Perimeter Network (Required)
Edge Servers are deployed on a perimeter network (also known as a DMZ, demilitarized zone, or screened subnet). The perimeter network is a small network set up separately from your organization's internal network and the Internet. The perimeter network allows external users access to the Edge Servers while preventing access to the internal corporate network.
You can deploy your perimeter network using two firewalls or one. The two-firewall configuration is recommended. For details about firewall requirements and other guidelines for deploying the perimeter network, see Infrastructure Requirements for External User Access.
Reverse HTTP Proxy
We recommend that you deploy a reverse HTTP proxy in the perimeter network. The reverse proxy is required for the following:
- To enable external users to download meeting content for your
meetings
- To enable external users to expand distribution groups
- To enable remote users to download files from the Address Book
Server or submit queries to the Address Book Web Query service
- To enable clients and devices outside your organization’s
intranet to obtain updates
If you already have a reverse proxy deployed to support
other services, you can use it for Office Communications Server
2007 R2 as well (although it must be deployed in the perimeter
network). The reverse proxy can be deployed using Microsoft
Internet Security and Acceleration (ISA) Server 2006, or other
Internet server software. For details, including steps for
configuring a server that is running ISA Server 2006 as a reverse
proxy, see
Director
If your organization is going to enable external access, we recommend that you deploy a Director.
A Director is a Standard Edition server or Enterprise pool that does not home users; instead, it serves as an internal next-hop server to which an Edge Server routes inbound SIP traffic destined to internal servers. The Director authenticates inbound requests and distributes them among the servers in the Enterprise pool or to the appropriate Standard Edition server.
By authenticating inbound SIP traffic from remote users, the Director relieves Enterprise pool servers from the overhead of performing authentication of remote users. It also helps insulate home servers and Enterprise pools from malicious traffic such as denial-of-service attacks; if the network is flooded with invalid external traffic in such an attack, this traffic ends at the Director, and internal users should not see any effect on performance.
 Supported Topologies
Supported Topologies
Each Edge Server always runs all three Edge Server services: Access Edge service to validate external users and enable instant messaging (IM), Web Conferencing Edge service to enable external users to join on-premises meetings, and A/V Edge service to enable the sharing of audio and video with external users, and enable Desktop Sharing with external users.
You can configure one or more Edge Servers on your network, according to your performance needs. Three Edge Server topologies are supported: single consolidated edge topology, scaled consolidated edge topology, and multiple-site consolidated edge topology.
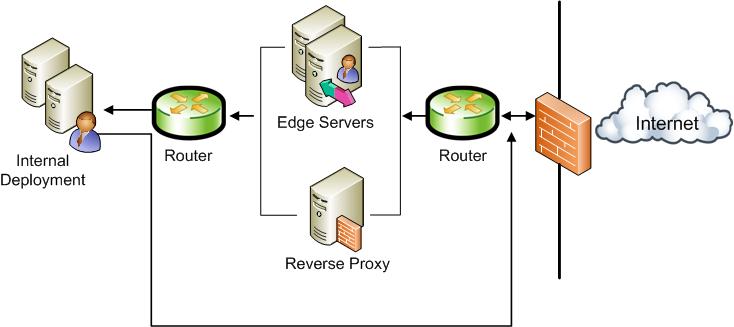
Single Consolidated Edge
In this topology, a single Edge Server computer is deployed in the data center, as shown in Figure 1.
Figure 1. Single consolidated edge topology

Scaled Consolidated Edge
In this topology, two or more Edge Server computers are deployed in the data center, with a load balancer between the perimeter network and the Internet, and another load balancer between the perimeter network and the internal network, as shown in Figure 2.
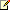 Note: Note: |
|---|
| The load balancer deployed between the perimeter network and the internal network must be configured to only load-balance the traffic to the Access Edge service and the A/V Edge service; it cannot load-balance the traffic to the Web Conferencing Edge service. |
Figure 2. Scaled consolidated edge topology
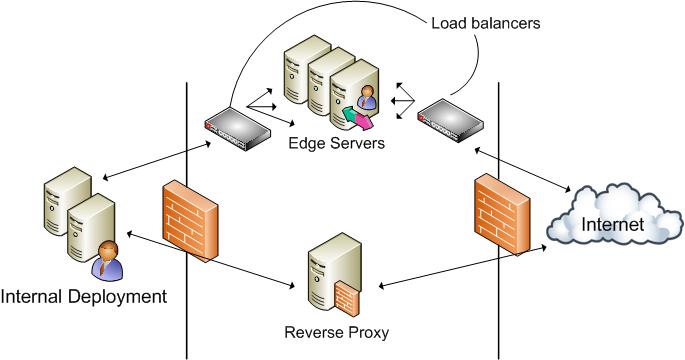
Multiple Site Consolidated Edge
In this topology, the data center has a scaled consolidated edge topology, and one or more remote sites deploy a single consolidated edge topology or a scaled consolidated edge topology, as shown in Figure 3.
Figure 3. Multiple-site consolidated edge topology
 Firewall Topologies
Firewall Topologies
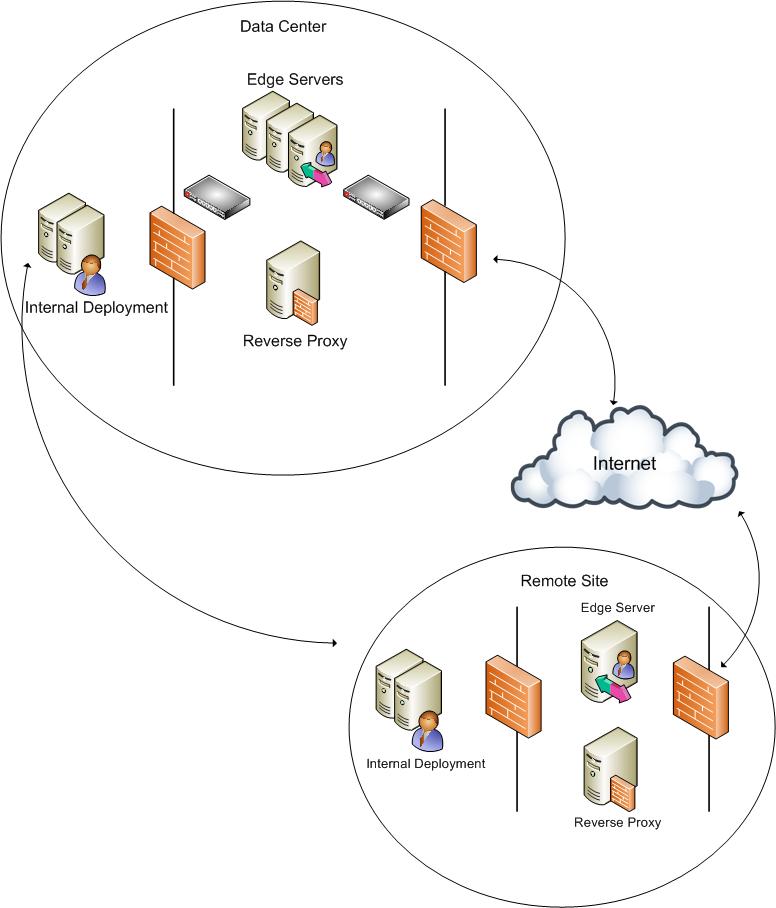
The recommended topology includes setting up your perimeter network between two firewalls: an external firewall and an internal firewall (as shown in Figure 1). Using two firewalls ensures strict routing from one network edge to the other, and it protects your internal network behind two levels of firewall.
A deployment using only one firewall (as shown in Figure 4) is also supported.
Figure 4. Single-firewall edge topology
 Collocation
Collocation
Edge Server cannot be collocated with any other Office Communications Server role.
 Hardware and Software
Requirements
Hardware and Software
Requirements
For a list of hardware and software requirements for Edge Servers and Directors, see Internal Office Communications Server Component Requirements.
 Scaling
Scaling
To scale your Edge Server capabilities, simply deploy more Edge Servers in your perimeter network, and use a load balancer to spread the workload among them.
If you use a multiple-site topology, you can deploy multiple Edge Servers both in your data center and in any remote sites that require such scaling.






