 Supported Topologies
Supported Topologies
For the purposes of this walkthrough, we shall define two sample topologies to illustrate specific steps that would be involved in moving to a load-balanced Enterprise pool. They are shown in the figures below. The first shows a one-armed topology, and the second shows a two-armed topology. These are the only two topologies that are supported in Office Communications Server 2007 R2. Note that the IP addresses of the corresponding servers in both diagrams are the same. The key difference is the networking topology and routing. In particular, notice the difference in subnets between the two diagrams.
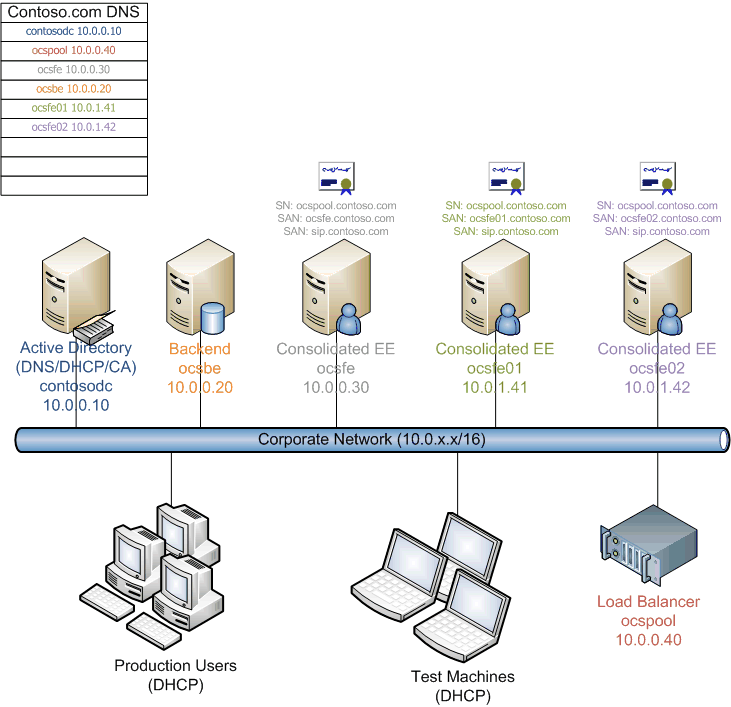
Figure above: One-Armed topology
Your networking team may have an existing best practice for deploying load balanced services, and that will probably have the biggest impact on which option that you will use. If no precedent exists, here are some factors to consider when deciding between a one-armed or two-armed topology.
One Armed Topology
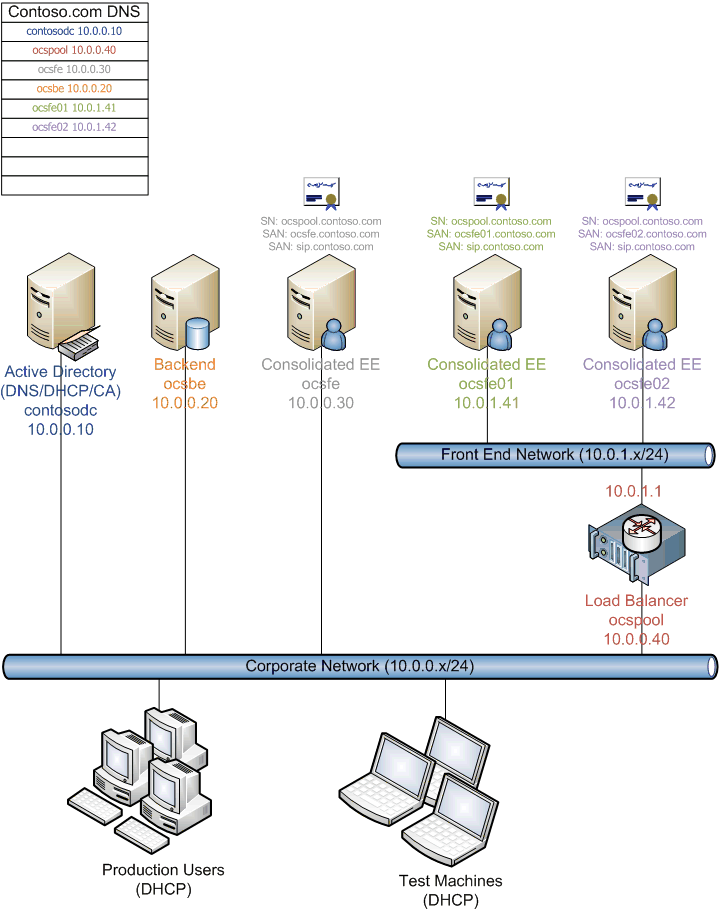
Figure above: Two-Armed topology
A one-armed topology is easier to deploy from a networking perspective, because it resides on the same network as the Front End Servers and does not introduce any additional changes in routing; however, not all traffic goes through the virtual IP address (VIP) of the load balancer (media between clients and conferencing servers, for example). If one function of the load balancer is to be a firewall between the corporate network and the load-balanced servers, the one-armed topology will not suffice. One benefit of this topology is that it is easier to the Front End Server functionality independent of the load balancer, because there is no dependency on the routing functionality of the load balancer.
Two-Armed Topology
A two-armed topology means that the Front End Servers reside behind the load balancer on a private network. The intent is to abstract away the Front End Servers from the main networking environment; however, these Front End Servers cannot truly be hidden by the load balancers VIPs alone, because clients need to contact the Front End Servers directly (for example, to establish media with conferencing servers), and the Front End Servers need to interact with other server components in the main network (for example, to look up Active Directory settings). As a result, the networking environment must be altered so that the load balancer is actually routing packets between the main and private networks. Additionally, the private network needs to use an IP address range that is routable within the corporation. This topology does enable the load balancer to be a single point of entry for all packets to and from the Front End Servers, and so performing firewall functionality is possible in the two-armed topology. The networking load will be considerably higher in the two-armed topology, because all traffic destined for the Front End Servers goes through the LOAD BALANCER.






