Topic Last Modified: 2010-07-19
Use the following Firewall and Port flowchart to determine firewall requirements and which ports to open. Then, review the network address translation (NAT) terminology because NAT can be implemented in many different ways. For a detailed example of firewall port settings, refer to the reference architectures in the Topologies for External User Access section.
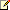 Note: Note: |
|---|
| Regarding the 50,000-59,999 port range, the best practice for Communications Server 2010 is to open it outbound for RDP/TCP for the A/V Edge external interface if corporate policy allows. |
 NAT Requirements for External
User Access
NAT Requirements for External
User Access
NAT is typically a routing function but with newer devices, firewalls and even hardware load balancers can be configured for network address translation, so rather than focus on which device is performing NAT, we will describe the required NAT behavior instead.
Microsoft Communications Server 2010 does not support NAT for traffic to/from the Edge internal interface, but for the Edge external interface, the following NAT behavior is required. This documentation uses the acronyms ChangeDST and ChangeSRC in tables and drawings to define the following required behavior:
- ChangeDST – the process of changing the destination IP address
on packets destined for the network that is using NAT. This is also
known as transparency, port forwarding, destination NAT mode, or
Half-NAT mode.
- ChangeSRC – the process of changing the source IP address on
packets leaving the network that is using NAT. This is also known
as proxy, secure NAT, stateful NAT, source NAT or Full-NAT
mode.
 Important: Important: |
|---|
| Some vendors define the process described in ChangeSRC as Source NAT (SNAT) or Full-NAT, which changes both the source and destination IP addresses on traffic leaving the network that is using NAT, but that is not case for Edge. The Edge Media Relay Authentication Server (MRAS) changes only the source IP address on packets leaving the Edge external interface. |
Regardless of the naming convention used, the NAT behavior required for the Edge server external interface is as follows:
- For traffic from the Internet to the Edge external
interface:
- Change the destination IP address of the incoming packet from
the Edge external interface public IP address to the translated IP
address of the Edge external interface.
- Leave the source IP address intact so that there is a return
route for the traffic.
- Change the destination IP address of the incoming packet from
the Edge external interface public IP address to the translated IP
address of the Edge external interface.
- For traffic from the Edge external interface to the
Internet:
- Change the source IP address of the packet leaving the Edge
external interface, from the translated IP address to the public IP
address of the Edge external interface so that the internal Edge IP
address is not exposed and because it is a non-routable IP
address.
- Leave the destination IP address intact on the outgoing
packets.
- Change the source IP address of the packet leaving the Edge
external interface, from the translated IP address to the public IP
address of the Edge external interface so that the internal Edge IP
address is not exposed and because it is a non-routable IP
address.
The following figure shows the distinction between changing the destination IP address (ChangeDST) for inbound traffic and changing the source IP Address (ChangeSRC) for outbound traffic using the A/V edge as an example.
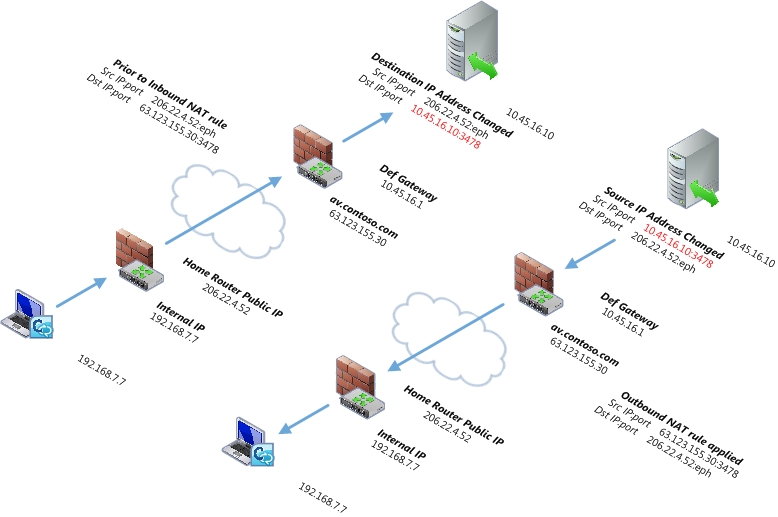
The key points are:
- For traffic incoming to the A/V Edge, the source IP address and
port do not change but the destination IP address changes from
63.123.155.30 to the translated IP address of 10.45.16.10.
- For traffic outbound from the A/V Edge back to the workstation,
the source IP address changes from that of the workstation’s public
IP address to that of the A/V Edge’s private IP address. And the
destination IP remains the workstation’s public IP address. Once
the packet leaves the first NAT device outbound, the rule on the
NAT device will change the source IP address from the A/V Edge’s
private IP address (10.45.16.10) to its public IP address
(63.123.155.30).
 A/V Edge Service Port Range
Requirements
A/V Edge Service Port Range
Requirements
In most cases, the A/V Edge service requires that external firewall rules allow RTP/TCP and RTP/UDP traffic in the 50,000 through 59,999 port range to flow in one or both directions. For example, opening this port range is required to support certain federation scenarios and the table below provides the details for each scenario. The table assumes that Communications Server 2010 is the primary federation partner and is being configured to communicate with one of the three federation partner types listed.
A/V Edge Service Port Range (50,000 – 59,999) Requirements
| Federation Partner | RTP/TCP (inbound) | RTP/TCP (outbound) | RTP/UDP (inbound) | RTP/UDP (outbound) | ||
|---|---|---|---|---|---|---|
|
Microsoft Communications Server 2010 |
N/A |
Open if Application Sharing or file transfer is required. A/V will use STUN/TCP/443 and STUN/UDP/3478 but the best practice is to open RTP/TCP 50,000-59,999 outbound. |
N/A |
N/A |
||
|
Microsoft Office Communications Server 2007 R2 |
N/A |
Open if Application Sharing, file transfer or A/V with the new version of Windows Live Messenger is required
A/V will use STUN/TCP/443 and STUN/UDP/3478. |
N/A |
N/A |
||
|
Microsoft Office Communications Server 2007 |
Open |
Open |
Open |
Open |
 Note: Note: |
|---|
| (inbound) refers to RTP/TCP and RTP/UDP traffic from the
Internet to the A/V Edge external interface. (outbound) refers to RTP/TCP and RTP/UDP traffic from the A/V Edge external interface to the Internet. |

