Applies to: Exchange Server 2010 SP3, Exchange Server 2010 SP2
Topic Last Modified: 2012-09-24
Some legacy PBX telephony systems allow the caller to mark a voice mail message as private, blocking the intended recipient of the message from forwarding it to others when they listen to the message. In integrated voice mail systems, a voice message can be accessed in multiple ways, which makes it more of a challenge to prevent voice messages marked private from being exposed to unintended listeners.
Unified Messaging (UM) in Exchange Server 2010 can be configured to use Active Directory Rights Management Services (AD RMS) to protect voice messages for an organization. This feature is known as Protected Voice Mail.
When a voice message is protected, the recipient is not only blocked from forwarding the message, but UM also assures that only the intended recipient or recipients of the message can access its content. Protected voice messages can be accessed by using Microsoft Office Outlook 2010, Office Outlook Web App, and Exchange Server 2010 Outlook Voice Access.
Contents
Overview of Protected Voice Mail
Overview of Active Directory Rights Management Services
Client Support and End User Features
Protected Voice Mail Structure
Composing a Protected Voice Mail Message
SMS Notifications and Protected Voice Mail
Overview of Protected Voice Mail
The Protected Voice Mail feature is available with Exchange 2010 Unified Messaging (UM). It can be configured on a UM mailbox policy, and all Protected Voice Mail settings can be configured using the Exchange Management Console (EMC) or cmdlets in the Exchange Management Shell.
 Note: Note: |
|---|
| In a deployment where both Exchange 2010 servers and Microsoft Exchange Server 2007 servers exist, Voice Mail Preview isn't available to UM-enabled users who have an Exchange 2007 mailbox. |
Protected Voice Mail is implemented by applying Information Rights Management (IRM) to voice messages. When voice messages are protected by UM:
- Users can reply to protected voice messages.
- Recipients of a voice message can't forward it.
- Users can't save a copy of the voice message.
- Users can't save or copy the attached audio of the voice
message.
- A voice mail message can be opened only by the intended
recipient or recipients.
Both call answering voice mail messages and interpersonal voice messages (voice messages that are sent to a user using Outlook Voice Access) can be protected by UM. However, protection won't be applied to the following types of messages:
- Fax messages.
- Non-voice messages. For example, e-mail messages or meeting
requests, even when they're created using Outlook Voice Access
(voice replies).
Overview of Active Directory Rights Management Services
AD RMS, a component of Windows Server 2008, is available to help protect files so that only the users who the sender intends to view a file can do so. AD RMS protects a file by specifying the rights that a user must have to access the file. Rights can be configured to allow a user to open, modify, print, forward, or take other actions with the rights-managed information. With AD RMS, you can safeguard data when it's distributed outside your network.
An AD RMS system has both a server and a client component, including the following:
- A Windows Server 2008 R2–based server running the Active
Directory Rights Management Services server role, which handles
certificates and licensing.
- A database server.
- The AD RMS client. The latest version of the AD RMS client is
included as part of the Windows 7 and Windows Vista operating
systems.
The server component is made up of several Web services that run on a Microsoft server such as Windows Server 2008. The client component can be run on either a client or server operating system and includes functions that enable an application to encrypt and decrypt content, retrieve templates and revocation lists, and acquire licenses and certificates from a server.
By using AD RMS and the AD RMS client, you can augment an organization's security strategy by protecting information through persistent usage policies that remain with the information, regardless of where it's moved. You can use AD RMS to help prevent sensitive information—such as financial reports, product specifications, customer data, and confidential e-mail and voice mail messages—from intentionally or accidentally getting into the wrong hands. For detailed information, see AD RMS Overview.
In Exchange 2010, you can use Information Rights Management (IRM) features to apply persistent protection to messages and attachments. IRM uses AD RMS, an information protection technology in Windows Server 2008 and Windows Server 2008 R2. To use IRM to implement Protected Voice Mail, you need Windows Server 2008 R2 with AD RMS.
Using the IRM features in Exchange 2010, and Protected Voice Mail, your organization and your users can control the rights recipients have to access e-mail and voice mail messages. IRM can be also used to restrict recipient actions such as forwarding a message to other recipients, printing a message or attachment, or extracting message or attachment content by copying and pasting. For details, see Understanding Information Rights Management.
IRM Requirements
Before you can implement IRM in Exchange 2010, you must first deploy and configure your AD RMS infrastructure. For detailed information, see Active Directory Rights Management Services. To implement IRM to support Protected Voice Mail in your Exchange 2010 organization, your deployment must meet the following requirements.
| Server | Requirement |
|---|---|
|
AD RMS Cluster |
|
|
Exchange Server |
|
Configuring and Testing IRM
You must use the Shell to configure IRM features in Exchange 2010. To configure individual IRM features, use the Set-IRMConfiguration cmdlet. For more information about how to configure IRM features, see Managing Information Rights Management.
After you've set up an Exchange 2010 server, you can use the Test-IRMConfiguration cmdlet to perform end-to-end tests of your IRM deployment. This cmdlet verifies the IRM configuration for an organization and should be run before enabling Protected Voice Mail. The Test-IRMConfiguration cmdlet performs the following tests:
- Inspects the IRM configuration for your Exchange 2010
organization
- Checks the AD RMS server for version and hotfix information
- Verifies whether an Exchange server can be activated for RMS by
retrieving a Rights Account Certificate and Client Licensor
Certificate (CLC)
- Acquires AD RMS rights policy templates from the AD RMS
server
- Verifies that the specified sender can send IRM-protected
messages
- Retrieves a super user use license for the specified
recipient
- Acquires a pre-license for the specified recipient
Client Support and End User Features
The e-mail client software that's used to listen to a Protected Voice Mail message must support IRM and know how to read a UM-protected voice message. E-mail clients that are supported include Microsoft Outlook 2010, Outlook Web App, and Exchange 2010 Outlook Voice Access. The following table contains a list of e-mail clients and whether or not they're supported.
| E-mail client | Description |
|---|---|
|
Microsoft Outlook |
|
|
Outlook Web App |
|
|
Outlook Voice Access |
|
|
Windows Mobile |
|
|
Other e-mail clients |
|
Protected Voice Message Structure
There are actually two messages involved for each Protected Voice Mail message. The first message is the outer message, which isn't encrypted. It contains an attachment named message.rpmsg. The attachment contains the IRM-protected voice message and internal rights management control data. The Rights Management Control data includes a content key, and rights information that specifies who can access the voice message and how those users can access it.
Protected voice messages are shown in the user's Inbox in the Voice Mail search folder. The user can listen to the voice messages by using the embedded audio player just as they would listen to a regular voice message, except that the Forward button will be disabled and a note will be shown at the top of the message stating that it's protected and that it can't be forwarded.
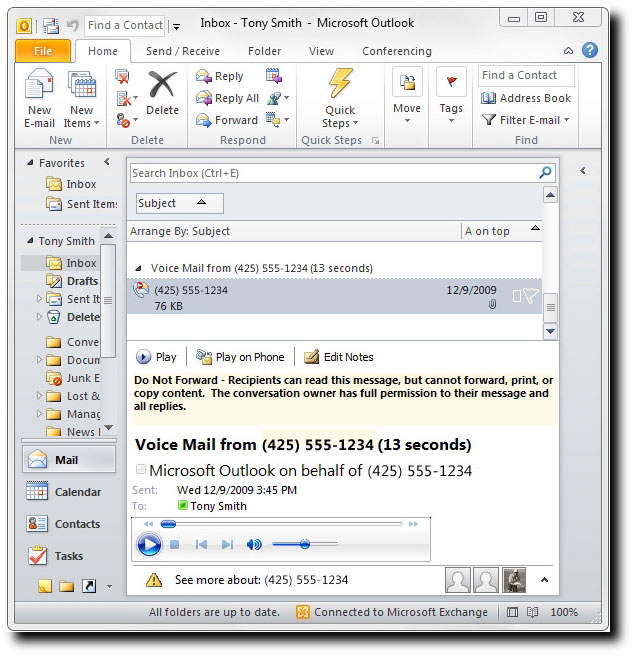
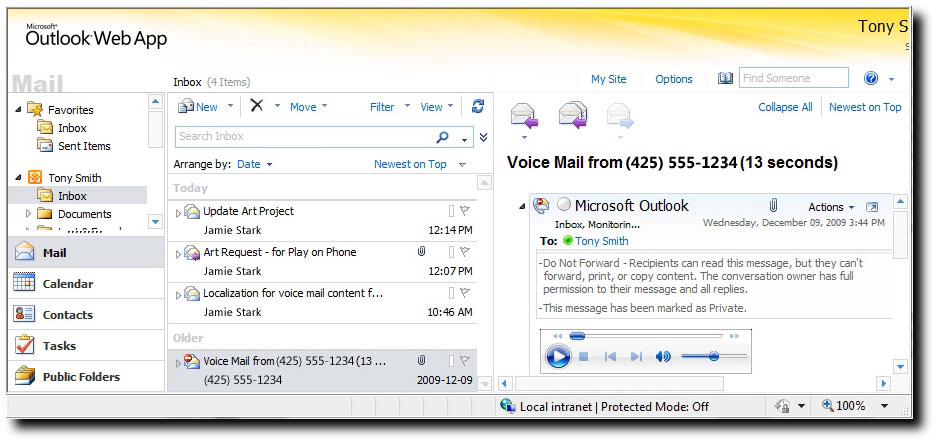
For e-mail clients that don't support Protected Voice Mail, the body of the outer message will be displayed. Default text is provided by UM when the protected voice message is being created. Administrators can overwrite this text by using the UM mailbox policy configuration objects.
If the user is using an e-mail client that doesn't support Protected Voice Mail, the following default text will appear on the user's client application e-mail form: "Your e-mail program doesn't support opening voice messages that are sent with restricted permission. To listen to this message, use Outlook 2010 or Outlook Web App in Exchange 2010. Or, if you're using Exchange 2010 Unified Messaging, you can use Outlook Voice Access."
You can customize the default text that's included in the e-mail message by configuring a UM mailbox policy. For example, you could configure the UM mailbox policy with customized text such as, "You can't open this voice mail message because it's protected. To view or listen to this voice message, sign in to your mailbox at https://mail.contoso.com or call +1 (425) 555-1234 to call in to Outlook Voice Access."
Composing a Protected Voice Mail Message
There are two situations in which protected voice messages can be created:
- Call Answering Call answering occurs
when a caller calls a UM-enabled user, but the user isn't available
to answer the call or forwards it directly to his or her voice
mail. In call answering scenarios, the voice mail system will play
a series of voice prompts after the caller records their voice mail
message.
The caller can then choose from additional message options, including the option to mark the voice message as private by pressing the pound (#) key. If the caller pressed the # key, they can follow the instructions provided by UM to mark the message as private, remove the private marking from the private voice message, or mark the voice message with High importance. The following diagram shows the menu options that are available to callers when they leave a private voice message for a user.
 Note:
Note:For call answering calls, the Protected Voice Mail settings on the UM mailbox policy of the intended recipient of the message are used by UM, because the caller isn't authenticated. 
- Outlook Voice Access Outlook Voice
Access lets UM-enabled users access their Exchange 2010 mailbox
using analog, digital, or cellular telephones by dialing their
Outlook Voice Access number. There are two Exchange 2010 Unified
Messaging user interfaces available to UM-enabled users: the
telephone user interface (TUI) and the voice user interface
(VUI).
Outlook Voice Access users can search for contacts in the directory and send them voice messages. If Protected Voice Mail has been enabled for the UM-enabled recipients, callers can mark the messages as private after they're recorded. Alternatively, administrators can configure a UM mailbox policy to ensure that all voice messages sent by authenticated users are protected by UM.
 Note:
Note:If a caller is authenticated, the Protected Voice Mail settings on the UM mailbox policy that is linked to the caller are applied, regardless the UM mailbox policy settings for the intended recipient of the voice mail message. 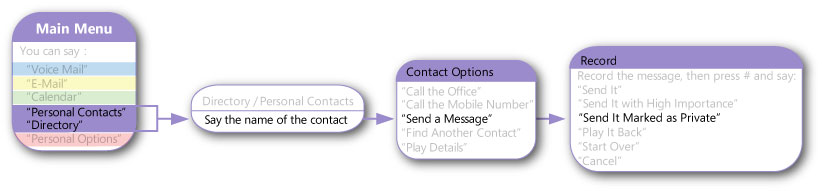

UM Mailbox Policies
You can create a Unified Messaging mailbox policy to apply a common set of UM policy settings, such as PIN policy settings, dialing restrictions, and Protected Voice Mail settings to a collection of UM-enabled mailboxes. To learn more about UM mailbox policies, see Managing UM Mailbox Policies.
You can use the EMC or the Exchange Set-UMMailboxPolicy cmdlet to configure Protected Voice Mail options. The following table lists the settings that can be configured for Protected Voice Mail.
Protected Voice Mail settings
| Shell Parameter | Setting available in EMC? | Description |
|---|---|---|
|
ProtectAuthenticatedVoiceMail |
Yes |
The ProtectAuthenticatedVoiceMail parameter specifies
whether UM-enabled users can send protected voice messages when
they're accessing their mailbox using Outlook Voice Access. The
default setting is |
|
ProtectUnauthenticatedVoiceMail |
Yes |
The ProtectUnauthenticatedVoiceMail parameter specifies
whether the Unified Messaging servers that answer calls for
UM-enabled users associated with a UM mailbox policy create
protected voice messages. This setting also applies when a message
is sent from a UM auto attendant to a UM-enabled user. The default
setting is |
|
ProtectedVoiceMailText |
Yes |
The ProtectedVoiceMailText parameter specifies the text
to be included in the body of the outer message of a Protected
Voice Mail message. This text will be shown in all e-mail client
applications that don't support Protected Voice Mail messages. Note
that a default message is always provided by UM when this property
is set to |
|
RequireProtectedPlayOnPhone |
Yes |
The RequireProtectedPlayOnPhone parameter specifies
whether users associated with the UM mailbox policy will be forced
to listen to the protected voice message over the phone (using Play
On Phone). The default value is |
|
AllowVoiceResponseToOtherMessageTypes |
Yes |
The AllowVoiceResponseToOtherMessageTypes parameter specifies whether callers who have authenticated to Outlook Voice Access to access their e-mail will be able to compose a voice reply to e-mails and meeting requests. |
For more information about how to manage Protected Voice Mail settings, see the following topics:
- Configure
Protected Voice Mail from Authenticated Callers on a UM Mailbox
Policy
- Configure
Protected Voice Mail from Unauthenticated Callers on a UM Mailbox
Policy
- Enable or
Disable Multimedia Playback of Protected Voice Messages on a UM
Mailbox Policy
- Specify the
Text to Display for E-Mail Clients that Don't Support Windows
Rights Management on a UM Mailbox Policy
- Set-UMMailboxPolicy
SMS Notifications and Protected Voice Mail
Users who configure their UM account to send SMS (also called text message) notifications to their mobile phone when voice messages are received will also receive audio transcription (Voice Mail Preview) text as part of the body of the text message. However, for protected voice messages, this represents a security issue because the content of the voice messages should always be protected.
When UM creates a text message notification for a voice message that's protected, it checks whether the voice message is marked as Private. If so, it won't add the transcribed audio text to the text message that it sends to the mobile phone. The following text will be included in the text message instead: "Use Outlook Voice Access to access this protected voice mail message."

