Applies to: Exchange Server 2013, Exchange Server, Exchange Online
Topic Last Modified: 2014-03-26
New in Exchange 2013 SP1, hybrid deployments are now supported for organizations with multiple on-premises Active Directory forests and a single Office 365 tenant. For hybrid deployment features and considerations, multi-forest organizations are defined as organizations having Exchange servers deployed in multiple Active Directory forests. Organizations that utilize a resource forest for user accounts, but maintain all Exchange servers in a single forest, aren’t classified as multi-forest in hybrid deployment scenarios. These types of organizations should consider themselves a single forest organization when planning and configuring a hybrid deployment.
For more information about hybrid deployments, see Exchange Server 2013 Hybrid Deployments
Multi-forest hybrid deployment prerequisites
Multi-forest hybrid deployment prerequisites are virtually identical to the hybrid deployment prerequisites for a single-forest organization, with the following exceptions:
-
Autodiscover Each Exchange forest must be authoritative for at least one SMTP namespace and the corresponding Autodiscover namespace. If there are shared domains across multiple Exchange forests, both mail routing and Autodiscover endpoints need to be configured and working properly between the Exchange forests before configuring your multi-forest hybrid deployment. The Office 365 service must be able to query the Autodiscover service in each Exchange forest.
-
Certificates All hybrid deployments require a digital certificate issued by trusted third-party certificate authority (CA). For a multi-forest hybrid deployment, a single digital certificate can’t be used for multiple Active Directory forests. Each forest must use a dedicated CA-issued certificate for secure mail transport to function correctly in a hybrid deployment. The certificate used for hybrid deployment features for each forest in a multi-forest organization must differ in at least one of the following properties:
-
Common Name The common name (CN) of the digital certificate is part of the certificate subject. This must match the host being authenticated and is typically the external hostname for the Client Access server in the Active Directory forest. For example, mail.contoso.com. We recommend using the CN as the differentiating property between Active Directory certificates used in multi-forest hybrid deployments.
-
Issuer The third-party CA that verified the organization information and issued the certificate. For example, VeriSign or Go Daddy. For example, one forest would have a certificate issued by VeriSign and one forest would have a certificate issued by Go Daddy.
 Important:
Important:The certificate installed on the Mailbox and Client Access (and Edge Transport if deployed) servers in each Active Directory forest used for mail transport in the hybrid deployment must all be issued by the same CA and have the same common name. -
-
Exchange servers At least one Exchange 2013 SP1 server with the Client Access server role must be installed in each Active Directory forest configured for hybrid deployment. The Client Access server is the inbound secure mail transport endpoint for the Exchange Online Protection (EOP) service included with the Office 365 tenant service and enables the Hybrid Configuration wizard to run in the Active Directory forest. Additionally, at least one Exchange 2013 SP1 server with the Mailbox server role must be installed in each Active Directory forest configured for hybrid deployment. The Mailbox server is the outbound secure mail transport endpoint for messages sent to the EOP service and the Exchange Online organization.
-
Active Directory synchronization All hybrid deployments require Active Directory synchronization with Office 365. For multi-forest on-premises Exchange organizations to configure a hybrid deployment with a single Office 365 tenant, on-premises organizations are required to deploy Microsoft Forefront Identity Manager (FIM) 2010 R2 or greater and the Windows Azure Active Directory (AAD) connector.
For more information, see Multi-forest Directory Sync with Single Sign-On Scenario.
-
Single sign-on Although not a requirement for hybrid deployments with single Active Directory forests, single sign-on (SSO) is a requirement for multi-forest hybrid deployments. SSO enables users to access both the on-premises and Exchange Online organizations with a single user name and password. SSO also provides users with a familiar sign-on experience and allows administrators to easily control account policies for Exchange Online organization mailboxes by using on-premises Active Directory management tools. Administrators can choose to configure a SSO server in each Active Directory forest, or to configure a single SSO server if there is a two-way forest trust configured between the on-premises forests.
For more information, see Single sign-on with hybrid deployments.
For a full listing of hybrid deployment prerequisites, see Hybrid deployment prerequisites
Multi-forest hybrid deployment scenario
Take a look at the following scenario. It's an example topology that provides an overview of a typical Exchange 2013 deployment. Contoso, Ltd. is a multi-forest, multi-domain organization with two Active Directory forests. Forest A contains the contoso.com domain and Forest B contains the sale.contoso.com domain. Each contains domain controllers in each forest, one Exchange 2013 SP1 server with the Client Access role installed, and one Exchange 2013 SP1 server with the Mailbox server role installed. Remote Contoso users use Outlook Web App to connect to Exchange 2013 over the Internet to check their mailboxes and access their Outlook calendar.
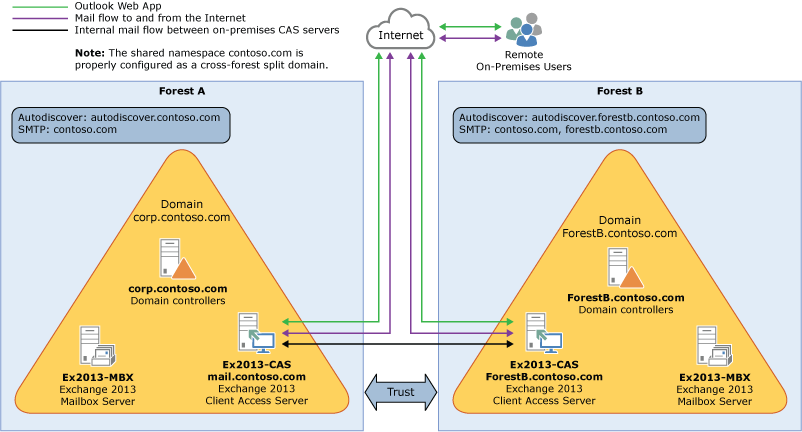
Let's say that you’re the network administrator for Contoso and you’re interested in configuring a hybrid deployment. You deploy and configure a required Active Directory Synchronization server in Forest A and you also decide to deploy an Active Directory Federation Services (AD FS) server as an option to minimize the number of prompts for account credentials for Contoso users and administrators accessing Office 365 services in Forest A. After you complete the hybrid deployment prerequisites and use the Hybrid Configuration wizard to select options for the hybrid deployment, your new topology has the following configuration:
-
Users will use their existing network account credentials for logging on to the on-premises and Exchange Online organizations (“single sign-on”).
-
User mailboxes located on-premises and in the Exchange Online organization will use multiple email address domains. For example, mailboxes located in Forest A on-premises and some mailboxes located in the Exchange Online organization will use @contoso.com in user email addresses and mailboxes in Forest B and some mailboxes located in the Exchange Online organization will use @sales.contoso.com.
-
All mail is delivered to the Internet by the on-premises organization. The on-premises organization controls all messaging transport and serves as a relay for the Exchange Online organization (“centralized mail transport”).
-
On-premises and Exchange Online organization users can share calendar free/busy information with each other. Organization relationships configured for both organizations also enable cross-premises message tracking, MailTips, and message search.
-
On-premises and Exchange Online users use the same URL to connect to their mailboxes over the Internet.
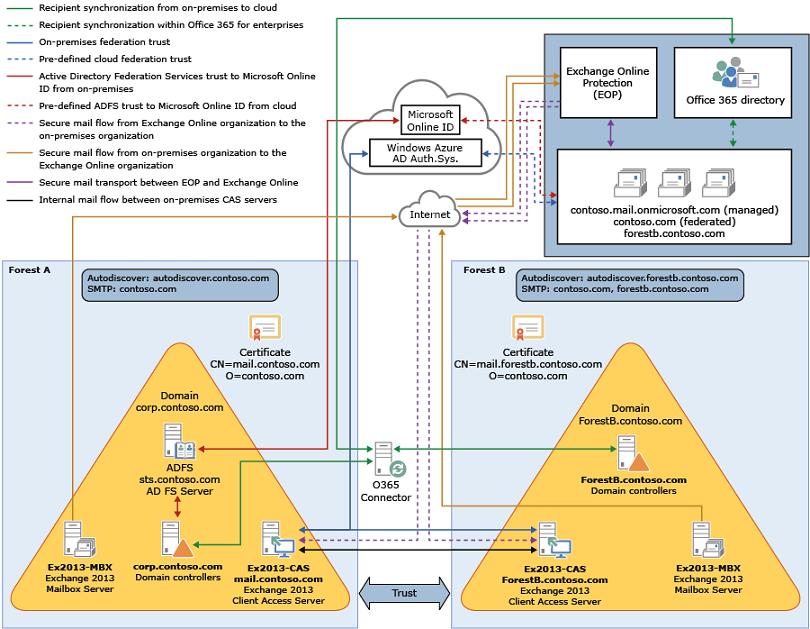
If you compare Contoso's existing organization configuration and the hybrid deployment configuration, you'll see that configuring a hybrid deployment has added servers and services that support additional communication and features that are shared between the on-premises and Exchange Online organizations. Here's an overview of the changes that a hybrid deployment has made from the initial on-premises Exchange organization.
| Configuration | Before hybrid deployment | After hybrid deployment |
|---|---|---|
|
Mailbox location |
Mailboxes on-premises only. |
Mailboxes on-premises and in Exchange Online. |
|
Message transport |
On-premises Client Access servers handle all inbound and outbound message routing. |
On-premises Client Access server handles internal message routing between the on-premises and Exchange Online organization. |
|
Outlook Web App |
On-premises Client Access server receives all Outlook Web App requests and displays mailbox information. |
On-premises Client Access server redirects Outlook Web App requests to either the on-premises Exchange 2013 SP1 Mailbox server or provides a link to log on to the Exchange Online organization. |
|
Unified GAL for both organizations |
Not applicable; single organization only. |
On-premises Active Directory synchronization server replicates Active Directory information for mail-enabled objects to the Exchange Online organization. |
|
Single-sign on used for both organizations |
Not applicable; single organization only. |
On-premises Active Directory Federation Services (AD FS) server supports using single-sign on credentials for mailboxes located either on-premises or in the Office 365 organization. |
|
Organization relationship established and a federation trust with Windows Azure AD authentication system |
Trust relationship with the Windows Azure AD authentication system and organization relationships with other federated Exchange organizations may be configured. |
Trust relationship with the Windows Azure AD authentication system is required. Organization relationships are established between the on-premises and Exchange Online organization. |
|
Free/busy sharing |
Free/busy sharing between on-premises users only. |
Free/busy sharing between both on-premises and Exchange Online users. |
Configuring hybrid deployments in multi-forest organizations
To configure a hybrid deployment for a multi-forest organization, you’ll need to complete the basic steps below:
-
Verify that you’ve met the hybrid deployment prerequisites. See the prerequisites listed earlier in this topic and Hybrid deployment prerequisites. Typically, only one forest needs an Active Directory synchronization server installed. An AD FS server must be installed in each forest to enable single sign-on if a two-way forest trust isn’t configured between the forests.
-
Obtain a third-party CA certificate for each Active Directory forest that meets the requirements listed previously in this topic.
-
Install the certificate on all Exchange 2013 SP1 Client Access and Mailbox servers in each forest.
-
Complete the steps outlined in the Create a hybrid deployment with the Hybrid Configuration wizard topic for the primary forest.
 Important:
Important:Be sure to select the certificate designated for the primary forest in the Hybrid Configuration wizard and select the primary SMTP domain for the forest. -
Complete the steps outlined in the Create a hybrid deployment with the Hybrid Configuration wizard topic for the secondary forest.
 Important:
Important:Be sure to select the certificate designated for the secondary forest in the Hybrid Configuration wizard and select the primary SMTP domain for the forest.

