MDaemon supports both Sender Policy Framework (SPF) and Sender ID Framework (SIDF) to help verify sending servers and protect against spoofing and phishing, which are two common types of email forgery in which the sender of the message attempts to make the message appear to be coming from someone else.
Many domains publish MX records in the Domain Name System (DNS) to identify the locations permitted to receive mail for them, but this doesn't identify the locations allowed to send mail for them. SPF is a means whereby domains can also publish sender records to identify those locations authorized to send messages. By performing an SPF lookup on incoming messages, MDaemon can attempt to determine whether or not the sending server is permitted to deliver mail for the purported sending domain, and consequently determine whether or not the sender's address may have been forged or "spoofed". Sender ID is related to SPF, but it is more complex in order to more reliably determine the actual domain purported to have sent the message, and to reduce the likelihood of incorrect results.
Use the options on this tab to configure your server's SPF and Sender ID settings.
For more information on SPF, visit:
For more information on Sender ID, visit:
http://www.microsoft.com/mscorp/safety/technologies/senderid/default.mspx
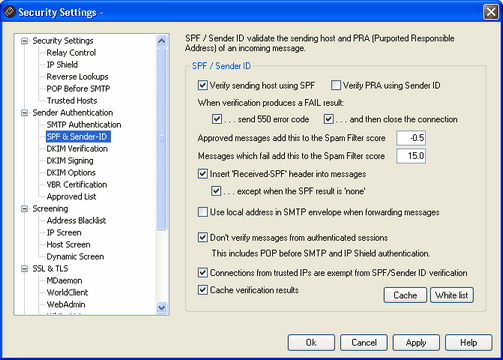
SPF / Sender ID
Verify sending host using SPF
When this option is enabled, MDaemon will perform queries for SPF data on the sending host of any incoming messages that do not come from white listed IP addresses or exempt sessions, such as authenticated connections or trusted IP addresses (when those exemptions have been enabled). The host MDaemon will verify is taken from the MAIL value passed during SMTP processing This SPF verification option is enabled by default.
Verify PRA using Sender ID
Enable this option if you wish to use the Sender ID framework to verify incoming messages. MDaemon will identify the Purported Responsible Address (PRA) of the incoming message through careful inspection of its headers and then verify whether or not the message originated from that location. The PRA is the most recent address purported to be responsible for the message, which may or may not be its original sender.
When verification produces a FAIL result:
...send 550 error code
Click this check box if you want a 550 error code to be sent when the result of the SPF/Sender ID query is "Fail".
...and then close the connection
Enable this option if you want the connection to be closed immediately after sending the 550 error code.
Approved messages add this to the Spam Filter score
Specify the amount that you wish to add to a message's Spam Score when SPF/Sender ID confirms that it originated from a domain found on the Approved List.
|
|
Ordinarily the value specified here should be a negative number so that the spam score will be reduced for the approved messages. |
Messages which fail SPF add this to the Spam Filter score
Specify the amount that you wish to add to the message's Spam Score when it fails to pass SPF/Sender ID verification.
Insert 'Received-SPF' header into messages
Click this option if you want a "Received-SPF" header to be inserted into each message.
...except when the SPF result is 'none'
Enable this option if you do not wish the "Received-SPF" header to be inserted into a message when the result of the SPF query is "none".
Use local address in SMTP envelope when forwarding messages
Click this option if you want all mail forwarded by MDaemon to use a local address in the SMTP envelope. This helps reduce problems associated with forwarding. Normally, forwarded messages are sent using the email address of the original sender and not the email address that is actually doing the forwarding. In some situations, using a local address may be necessary in order to prevent the receiving server from falsely identifying the forwarded message as having a "spoofed" address.
Verification Options
Don't verify messages from authenticated sessions
Click this check box if you wish authenticated connections to be exempt from SPF/Sender ID queries. Authenticated sessions include those verified via SMTP Authentication, POP before SMTP, or the IP Shield.
Connections from trusted IPs are exempt from SPF/Sender ID verification
Enable this option if you want connections from trusted IP addresses to be exempt from SPF/Sender ID verification.
Cache verification results
Click this option if you wish to temporarily cache the results of SPF queries.
Cache
This button opens the SPF cache.
White List
Click this button to open the SPF white list on which you can designate IP addresses that you wish to exempt from SPF lookups.