Topic Last Modified: 2010-11-09
The Lync Server 2010 Edge functionality described in this reference architecture is very similar to what was first introduced in Office Communications Server 2007 R2, with the following exceptions:
- Port 4443 is used to route traffic from the reverse proxy
internal interface to the pool virtual IP (VIP).
- Port 4443 is used to route traffic from the pool Front End
Servers to the Edge internal interface.
There are several options for the 50,000 – 59,999 port ranges, but the following figure shows the common configuration for interoperability with previous versions of Office Communications Server. For details about the options for configuring this port range, see Determining External A/V Firewall and Port Requirements.
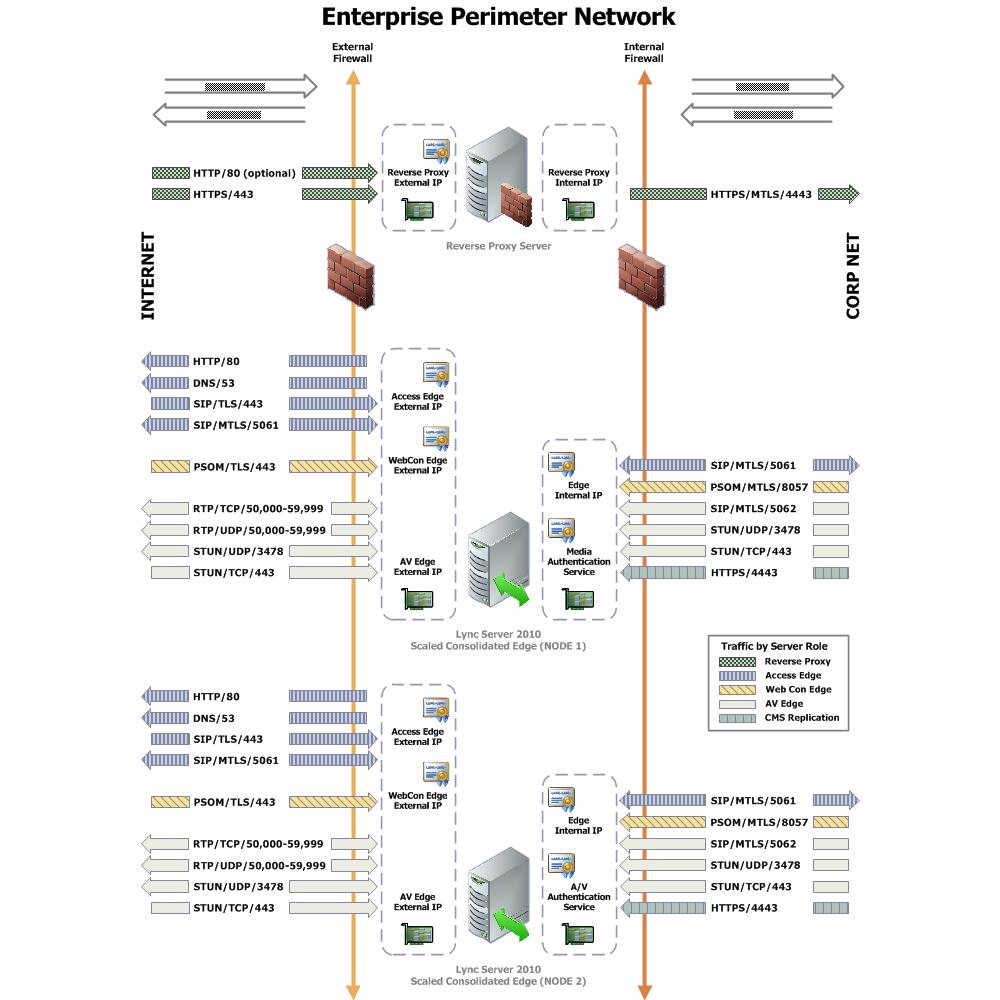
Firewall Summary for Single/Scaled Consolidated Edge with DNS Load Balancing: External Interface
| Protocol/port | Used for |
|---|---|
|
HTTP 80 (out) |
Checking certificate revocation lists |
|
DNS 53 (out) |
External DNS queries |
|
SIP/TLS/443 (in) |
Client-to-server SIP traffic for remote user access |
|
SIP/MTLS/5061 (in/out) |
Federation and connectivity with a hosted Exchange service |
|
PSOM/TLS/443 (in) |
Remote user access to conferences for anonymous and federated users |
|
RTP/TCP/50K range (in) |
Media exchange (for details, see Determining External A/V Firewall and Port Requirements) and Windows Live Messenger if public IM connectivity is enabled Required for Office Communications Server 2007 R2 interoperability |
|
RTP/TCP/50K range (out) |
Media exchange (for details, see Determining External A/V Firewall and Port Requirements) Required for Office Communications Server 2007 R2 interoperability Required for Office Communications Server 2007 R2 desktop sharing and federation Required for Lync Server 2010 application sharing, file transfer, or A/V with Windows Live Messenger |
|
RTP/UDP/50K range (in) |
Media exchange (for details, see Determining External A/V Firewall and Port Requirements) |
|
RTP/UDP/50K range (out) |
Media exchange (for details, see Determining External A/V Firewall and Port Requirements) or A/V with Windows Live Messenger Required for Office Communications Server 2007 interoperability |
|
STUN/MSTURN/UDP/3478 (in/out) |
External user access to A/V sessions (UDP) |
|
STUN/MSTURN/TCP/443 (in) |
External user access to A/V sessions and media (TCP) |
Firewall Details for Single/Scaled Consolidated Edge with DNS Load Balancing: Internal Interface
| Protocol/port | Used for |
|---|---|
|
SIP/MTLS/5061 (in/out) |
SIP traffic |
|
PSOM/MTLS/8057 (out) |
Web conferencing traffic from pool-to-Edge |
|
SIP/MTLS/5062 (out) |
Authentication of A/V users (A/V Authentication service) |
|
STUN/MSTURN/UDP/3478 (out) |
Preferred path for media transfer between internal and external users (UDP) |
|
STUN/MSTURN/TCP/443 (out) |
Alternate path for media transfer between internal and external users (TCP) |
|
HTTPS 4443 (out) |
Pushing Central Management store updates to Edge Servers |
When reading the preceding tables, (in) refers to traffic going from a less trusted network to a more trusted network, such as Internet-to-perimeter or perimeter-to-corporate). For example, traffic from the Internet to the Edge external interface or from the Edge internal interface to the next hop pool. (out) refers to traffic going from a more trusted network to a less trusted network, such as corporate-to-perimeter or perimeter-to-Internet). For example, traffic from a corporate pool to the Edge internal interface or from the Edge external interface to the Internet. And, (in/out) refers to traffic that is going both directions.
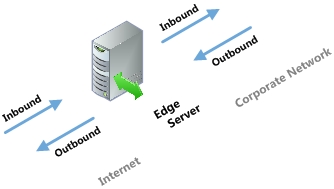
It is recommended that you only open the ports required to support the functionality for which you are providing external access.
For remote access to work for any edge service, it is mandatory that SIP traffic is allowed to flow bi-directionally as shown in the Inbound/Outbound edge traffic figure. Stated another way, the Access Edge service is involved in instant messaging (IM), presence, web conferencing, and audio/video (A/V).
Firewall Details for Reverse Proxy Server: External Interface
| Protocol/Port | Use for |
|---|---|
|
HTTP 80 (in) |
(Optional) Redirection to HTTPS if user accidentally enters http:// publishedSiteFQDN |
|
HTTPS 443 (in) |
Address book downloads, Address Book Web Query service, client updates, conference content, device updates, group expansion, dial-in conferencing, and conferences. |
Firewall Details for Reverse Proxy Server: Internal Interface
| Protocol/port | Used for |
|---|---|
|
HTTPS 4443 (in) |
Traffic sent to 443 on the reverse proxy external interface is redirected to a pool on port 4443 from the reverse proxy internal interface so that the pool web services can distinguish it from internal web traffic |
 Note: Note: |
|---|
| When reading the previous tables, (in) refers to traffic going from a less trusted network to a more trusted network, such as Internet-to-perimeter or perimeter-to-corporate). For example, traffic from Internet to the reverse proxy external interface or from the reverse proxy internal interface to a Standard Edition pool or a hardware load balancer VIP associated with a Front End pool. |
External Ports Settings Required for Scaled Consolidated Edge Topology (DNS Load Balanced): External Interface Node 1
| Edge role | Source IP address | Source port | Destination IP address | Destination port | Transport | Application | Notes |
|---|---|---|---|---|---|---|---|
|
Access |
10.45.16.10 |
Any |
Any |
80 |
TCP |
HTTP |
|
|
Access |
10.45.16.10 |
Any |
Any |
53 |
UDP |
DNS |
|
|
Access |
Any |
Any |
10.45.16.10 |
443 |
TCP |
SIP (TLS) |
Client-to-server SIP traffic for external user access |
|
Access |
Any |
Any |
10.45.16.10 |
5061 |
TCP |
SIP (MTLS) |
For federated and public IM connectivity using SIP |
|
Access |
10.45.16.10 |
Any |
Any |
5061 |
TCP |
SIP (MTLS) |
For federated and public IM connectivity using SIP |
|
Web Conferencing |
Any |
Any |
10.45.16.20 |
443 |
TCP |
PSOM (TLS) |
|
|
A/V |
10.45.16.30 |
50,000 – 59,999 |
Any |
Any |
TCP |
RTP |
Required only for desktop sharing with partners running Office Communications Server 2007. Also required for application sharing or file transfer with Lync Server 2010 federated users and A/V sessions with Windows Live Messenger. |
|
A/V |
10.45.16.30 |
50,000 – 59,999 |
Any |
Any |
UDP |
RTP |
Required only for federation with partners still running Office Communications Server 2007. |
|
A/V |
Any |
Any |
10.45.16.30 |
50,000 – 59,999 |
TCP |
RTP |
Required only for federation with partners still running Office Communications Server 2007. |
|
A/V |
Any |
Any |
10.45.16.30 |
50,000 – 59,999 |
UDP |
RTP |
Required only for federation with partners still running Office Communications Server 2007. |
|
A/V |
10.45.16.30 |
3478 |
Any |
3478 |
UDP |
STUN/MSTURN |
3478 outbound is used to determine the version of Edge Server that Lync Server 2010 is communicating with and also for media traffic from Edge Server-to-Edge Server. Required for federation with Lync Server 2010, Windows Live Messenger, and Office Communications Server 2007 R2, and also if multiple Edge pools are deployed within a company. |
|
A/V |
Any |
Any |
10.45.16.30 |
3478 |
UDP |
STUN/MSTURN |
|
|
A/V |
Any |
Any |
10.45.16.30 |
443 |
TCP |
STUN/MSTURN |
External Ports Settings Required for Scaled Consolidated Edge Topology (DNS Load Balanced): External Interface Node 2
| Edge role | Source IP address | Source port | Destination IP address | Destination port | Transport | Application | Notes |
|---|---|---|---|---|---|---|---|
|
Access |
10.45.16.11 |
Any |
Any |
80 |
TCP |
HTTP |
|
|
Access |
10.45.16.11 |
Any |
Any |
53 |
UDP |
DNS |
|
|
Access |
Any |
Any |
10.45.16.11 |
443 |
TCP |
SIP (TLS) |
Client-to-server SIP traffic for external user access |
|
Access |
Any |
Any |
10.45.16.11 |
5061 |
TCP |
SIP (MTLS) |
For federated and public IM connectivity using SIP |
|
Access |
10.45.16.11 |
Any |
Any |
5061 |
TCP |
SIP (MTLS) |
For federated and public IM connectivity using SIP |
|
Web Conferencing |
Any |
Any |
10.45.16.21 |
443 |
TCP |
PSOM (TLS) |
|
|
A/V |
10.45.16.31 |
50,000 – 59,999 |
Any |
Any |
TCP |
RTP |
Required only for desktop sharing with partners running Office Communications Server 2007. Also required for application sharing or file transfer with Lync Server 2010 federated users and A/V sessions with Windows Live Messenger. |
|
A/V |
10.45.16.31 |
50,000 – 59,999 |
Any |
Any |
UDP |
RTP |
Required only for federation with partners still running Office Communications Server 2007. |
|
A/V |
Any |
Any |
10.45.16.31 |
50,000 – 59,999 |
TCP |
RTP |
Required only for federation with partners still running Office Communications Server 2007. |
|
A/V |
Any |
Any |
10.45.16.31 |
50,000 – 59,999 |
UDP |
RTP |
Required only for federation with partners still running Office Communications Server 2007. |
|
A/V |
10.45.16.31 |
3478 |
Any |
3478 |
UDP |
STUN/MSTURN |
3478 outbound is used to determine the version of Edge Server that Lync Server 2010 is communicating with and also for media traffic from Edge Server-to-Edge Server. Required for federation with Lync Server 2010, Windows Live Messenger, and Office Communications Server 2007 R2, and also if multiple Edge pools are deployed within a company. |
|
A/V |
Any |
Any |
10.45.16.31 |
3478 |
UDP |
STUN/MSTURN |
|
|
A/V |
Any |
Any |
10.45.16.31 |
443 |
TCP |
STUN/MSTURN |
External Ports Settings Required for Scaled Consolidated Edge Topology (DNS Load Balanced): Reverse Proxy
| Edge role | Source IP address | Source Port | Destination IP address | Destination port | Transport | Application | Notes |
|---|---|---|---|---|---|---|---|
|
Reverse Proxy: N/A |
Any |
Any |
10.45.16.40 |
80 |
TCP |
SIP (TLS) |
(Optional) Can be used to redirect http traffic to https. |
|
Reverse Proxy: N/A |
Any |
Any |
10.45.16.40 |
443 |
TCP |
HTTPS |
Internal Firewall Ports Settings Required for Scaled Consolidated Edge Topology (DNS Load Balanced): Internal Interface Node 1
| Edge role | Source IP address | Source port | Destination IP address | Destination port | Transport | Application | Notes |
|---|---|---|---|---|---|---|---|
|
Access |
172.25.33.10 |
Any |
192.168.10.90 192.168.10.91 |
5061 |
TCP |
SIP (MTLS) |
Destination will be the next hop server(s). In the case of the reference architecture, it is the IP addresses of the two pool Front End Servers. |
|
Access |
192.168.10.90 192.168.10.91 |
Any |
172.25.33.10 |
5061 |
TCP |
SIP (MTLS) |
Source will be the next hop server(s). In the case of the reference architecture, it is the IP addresses of the two pool Front End Servers. |
|
Access |
192.168.10.90 192.168.10.91 |
Any |
172.25.33.10 |
4443 |
TCP |
HTTPS |
Used for Central Management store replication, include all Front End Servers. |
|
Web Conferencing |
Any |
Any |
172.25.33.10 |
8057 |
TCP |
PSOM (MTLS) |
|
|
A/V |
192.168.10.90 192.168.10.91 |
Any |
172.25.33.10 |
5062 |
TCP |
SIP (MTLS) |
Include all Front End Servers using this particular A/V Authentication service. |
|
A/V |
Any |
Any |
172.25.33.10 |
3478 |
UDP |
STUN/MSTURN |
|
|
A/V |
Any |
Any |
172.25.33.10 |
443 |
TCP |
STUN/MSTURN |
Internal Firewall Ports Settings Required for Scaled Consolidated Edge Topology (DNS Load Balanced): Internal Interface Node 2
| Edge role | Source IP address | Source port | Destination IP address | Destination port | Transport | Application | Notes |
|---|---|---|---|---|---|---|---|
|
Access |
172.25.33.11 |
Any |
192.168.10.90 192.168.10.91 |
5061 |
TCP |
SIP (MTLS) |
Destination will be the next hop server(s). In the case of the reference architecture, it is the IP addresses of the two pool Front End Servers. |
|
Access |
192.168.10.90 192.168.10.91 |
Any |
172.25.33.11 |
5061 |
TCP |
SIP (MTLS) |
Source will be the next hop server(s). In the case of the reference architecture, it is the IP addresses of the two pool Front End Servers. |
|
Access |
192.168.10.90 192.168.10.91 |
Any |
172.25.33.11 |
4443 |
TCP |
HTTPS |
Used for Central Management store replication, include all Front End Servers. |
|
Web Conferencing |
Any |
Any |
172.25.33.11 |
8057 |
TCP |
PSOM (MTLS) |
|
|
A/V |
192.168.10.90 192.168.10.91 |
Any |
172.25.33.11 |
5062 |
TCP |
SIP (MTLS) |
Include all Front End Servers using this particular A/V Authentication service. |
|
A/V |
Any |
Any |
172.25.33.11 |
3478 |
UDP |
STUN/MSTURN |
|
|
A/V |
Any |
Any |
172.25.33.11 |
443 |
TCP |
STUN/MSTURN |
Internal Firewall Ports Settings Required for Scaled Consolidated Edge Topology (DNS Load Balanced): Reverse Proxy
| Edge role | Source IP address | Source port | Destination IP address | Destination port | Transport | Application |
|---|---|---|---|---|---|---|
|
Reverse proxy: N/A |
172.25.33.40 |
Any |
192.168.10.190 |
4443 |
TCP |
HTTPS |


