How you configure your firewalls is largely dependent on the specific firewalls you use in your organization, but each firewall also has common configuration requirements that are necessary for Office Communications Server 2007 R2. Follow the manufacturer's instructions for configuring each firewall, along with the information in this section, which describes the settings that must be configured on the internal and external firewalls.
 Publicly Routable IP
Address
Publicly Routable IP
Address
In any location with multiple Edge Servers deployed behind a load balancer, the external firewall cannot function as a network address translation (NAT). However, in a site with only a single Edge Server deployed, the external firewall can be configured as a NAT.
If you do so, configure the NAT as a destination network address translation (DNAT) for inbound traffic—in other words, configure any firewall filter used for traffic from the Internet to the Edge Server with DNAT, and configure any firewall filter for traffic going from the Edge Server to the Internet (outbound traffic) as a source network address translation (SNAT). The inbound and outbound filters must map to the same public IP address and the same private IP address, as shown in Figure 1.
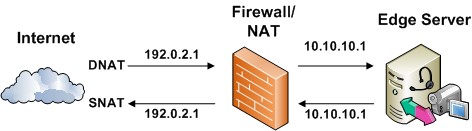
In all topologies, however, the internal firewall cannot act as a NAT for the internal IP address of any Edge Servers.
 Note: Note: |
|---|
In addition to being supported as a reverse proxy, Microsoft
Internet Security and Acceleration (ISA) Server is supported as a
firewall for Office Communications Server 2007 R2. The following
versions of ISA are supported as a firewall:
|
 Default Ports
Default Ports
The following figure shows the default firewall ports for each server in the perimeter network.
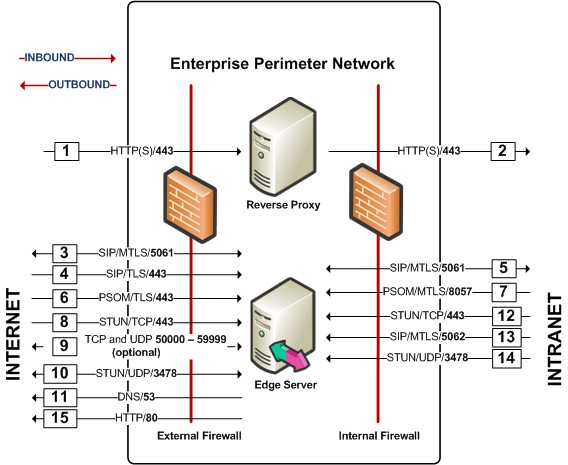
The following sections provide additional information about each port to be configured for each server role in each topology, as well as a mapping of the numbers in the previous figure to the respective port descriptions.
 Edge Server Firewall Policy
Rules
Edge Server Firewall Policy
Rules
The following three tables describe the firewall policy rules to be configured for the Edge Server. These settings are listed in separate tables to help illustrate which port settings are used by each service running on the Edge Server.
The following sections list the firewall policy rules that are required on each server in the perimeter network. In the tables in these sections, the numbers in the Figure mappingcolumn correspond to the numbers in Figure 2.
In the following tables, the direction for firewall policy rules that is indicated as outbound is defined as follows:
- On the internal firewall, it corresponds to traffic from
servers on the internal (private) network to the Edge Server in the
perimeter network.
- On the external firewall, it corresponds to traffic from the
Edge Server in the perimeter network to the Internet.
Table 1. Firewall Settings for the Access Edge Service
| Firewall | Policy rules | Figure mapping |
|---|---|---|
|
Internal |
Local Port: Any. Direction: Inbound (for remote user access and federation). Remote Port: 5061 TCP (TCP/MTLS). Local IP address: The internal IP address of the Access Edge service. Remote IP: The IP address of the next hop server. If a Director is deployed, use the IP address of the Director or VIP of the load balancer, if the Directors are load balanced. |
5 |
|
Internal |
Local Port: 5061 TCP (SIP/MTLS). Direction: Outbound (for remote user access and federation). Remote Port: Any. Local IP address: The internal IP address of the Access Edge service. Remote IP: If no Director is deployed, you may use any IP address. If a Director is deployed, use the IP address of the Director or the virtual IP address of the load balancer, if the Directors are load balanced. |
5 |
|
External |
Local Port: 5061 TCP (SIP/MTLS). Direction: Inbound/Outbound (federation). Remote Port: Any. Local IP: The external IP address of the Access Edge service. Remote IP: Any IP address. |
3 |
|
External |
Local Port: 443 TCP (SIP/TLS). Direction: Inbound (for remote user access). Remote Port: Any. Local IP: The external IP address of the Access Edge service. Remote IP: Any IP address. |
4 |
|
External |
Local Port: 53 DNS. Direction: Outbound (for DNS queries). Remote Port: Any. Local IP: The external IP address of the Access Edge service. Remote IP: Any IP address. |
11 |
|
External |
Local Port: 80 HTTP. Direction: Outbound (to download certificate revocation lists). Remote Port: Any. Local IP: The external IP address of the Access Edge service. Remote IP: Any IP address. |
15 |
 Note: Note: |
|---|
| Persistent Shared Object Model (PSOM) is the Microsoft proprietary protocol used for Web conferencing. |
Table 2. Firewall Settings for the Web Conferencing Edge Service
| Firewall | Policy rules | Figure mapping |
|---|---|---|
|
Internal |
Local Port: 8057 TCP (PSOM/MTLS) Direction: Outbound (for traffic between internal Web Conferencing Servers and the Web Conferencing Edge service) Remote Port: Any Local IP: The internal IP address of the Web Conferencing Edge service Remote IP: Any IP address |
7 |
|
External |
Local Port: 443 TCP (PSOM/TLS) Direction: Inbound (for access of remote, anonymous, and federated users to internal Web conferences) Remote Port: Any Local IP: The external IP address of the Web Conferencing Edge service Remote IP: Any IP address |
6 |
Table 3. Firewall Settings for the A/V Edge Service
| Firewall | Policy rules | Figure mapping | ||
|---|---|---|---|---|
|
Internal |
Local Port: 443 TCP (STUN/TCP). Direction: Outbound (for media transfer between internal users and external users). Remote Port: Any. Local IP: The internal IP address of the A/V Edge service. Remote IP: Any IP address. |
12 |
||
|
Internal |
Local Port: 5062 TCP (SIP/MTLS). Direction: Outbound (for authentication of A/V users). Remote Port: Any. Local IP: The internal IP address of the A/V Edge service. Remote IP: Any IP address. |
13 |
||
|
Internal |
Local Port: 3478 UDP (STUN/UDP). Direction: Outbound (for media transfer between internal users and external users). Note that this is the most likely setting required; because of the nature of UDP and different firewalls, your firewall may require different settings. Remote Port: Any. Local IP: The internal IP address of the A/V Edge service. Remote IP: Any IP address.
|
14 |
||
|
External |
Local Port: 443 TCP (STUN/TCP). Direction: Inbound (for external users’ access to media and A/V sessions). Remote Port: Any. Local IP: The external IP address of the A/V Edge service. Remote IP: Any IP address. |
8 |
||
|
External |
Local Port: 3478 UDP (STUN/UDP). Direction: Inbound/Outbound (for external users connecting to media or A/V sessions). Note that this is the most likely setting required; because of the nature of UDP and different firewalls, your firewall may require different settings. Remote Port: Any. Local IP: The external IP address of the A/V Edge service. Remote IP: Any IP address.
|
10 |
||
|
External |
Local Port Range: 50,000-59,999 TCP (RTP/TCP) (For details about this port range when federating with previous versions of Office Communications Server, see 50,000 - 59,999 Port Range.) Direction: Outbound (for media transfer). Remote Port: Any. Local IP: The external IP address of the A/V Edge service. Remote IP: Any IP address. |
9 |
 Reverse Proxy Firewall Policy
Rules
Reverse Proxy Firewall Policy
Rules
The following table describes the firewall policy to be configured for the reverse proxy.
Table 4. Firewall Settings for the Reverse Proxy
| Firewall | Policy rules | Figure mapping | ||
|---|---|---|---|---|
|
Internal |
Local Port: Any Direction: Inbound (for external user access to Web conferences) Remote Port: 443 TCP (HTTP(S)) Local IP: The internal IP address of the reverse proxy Remote IP: Any |
2 |
||
|
External |
Local Port: 443 TCP (HTTP(S)) Direction: Inbound Remote Port: Any Local IP address: The external IP address of the HTTP reverse proxy Remote IP: Any
|
1 |






