Topic Last Modified: 2010-07-18
In the Edge Server pool topology, two or more Edge Servers are deployed as a load-balanced pool in the perimeter network of the data center. DNS load balancing is used for traffic to both the external and internal Edge interfaces.
If your organization requires support for more than 5,000 Access Edge service client connections, 1,000 active Web Conferencing service client connections, or 500 concurrent A/V Edge sessions, and/or high availability of the Edge Server is important, this topology offers the advantages of scalability and failover support.
For simplicity, the following figure does not show any Directors deployed but in a real world production deployment they are recommended. For more information about the topology for Directors, see Components and Topologies for Director. The reverse proxy is also not load balanced but if it was, it would require a hardware load balancer. DNS load balancing is not an option for load balancing reverse proxy traffic.
 Note: Note: |
|---|
| For clarity, the .com DNS zone represents the external interface for both reverse proxy and consolidated edge servers, and the .net DNS zone refers to the internal interfaces. Depending on how your DNS is configured, both interfaces could be in the same zone (for example, in a split-brain DNS configuration). |

 Certificate Summary
Certificate Summary
Before proceeding, take a minute to map the entries in the table with the FQDNs/IP addresses shown in the Scaled Consolidated Edge Topology (DNS Load Balanced) figure so that the relationships are clear. For example, notice there is no certificate assigned to the A/V Edge external interface (av.contoso.com) but there is an A/V related certificate (avauth.contoso.net) assigned to the Media Authentication Service.
The certificates listed in the following table are required to support the edge topology shown in the Scaled Consolidated Edge Topology (DNS Load Balanced) figure. There are three certificates shown for the reverse proxy server to highlight the certificate requirements for dedicated simple URLs (for example, https://dial-in.contoso.com). For deployments that have a single pool or where multiple pools share the same dial-in conferencing and meeting simple URLs, you could create a single publishing rule and corresponding certificate. For example, URLs defined in topology builder as cs.contoso.com/dialin and cs.contoso.com/meet could share a single publishing rule and certificate with a subject name of cs.contoso.com. For details, see Simple URL Options.
 Note: Note: |
|---|
| The following table shows a second SIP entry in the Subject Alternate Name (SAN) list for reference. For each SIP domain in your organization, you need a corresponding FQDN listed in the certificate SAN list. |
 Important: Important: |
|---|
| The public certificate used on the Edge interfaces must be created as “exportable” and the same certificate must be assigned to each Edge server in the pool. |
Certificates Required for Scaled Consolidated Edge Topology (DNS Load Balanced)
| Component | Subject Name | Subject Alternate Name Entries/Order | CA | EKU | Assign To |
|---|---|---|---|---|---|
|
Scaled consolidated Edge |
access.contoso.com |
webcon.contoso.com sip.contoso.com sip.fabrikam.com |
Public |
Server/Client |
Assign a single certificate to the following Edge server roles: External Interface: Internal Interface: (using the Communications server Certificate Wizard) |
|
Reverse proxy |
csweb-ext.contoso.com |
N/A |
Public |
Server |
ABS, DGX, and IP Device publishing rules |
|
Reverse proxy |
dialin.contoso.com |
N/A |
Public |
Server |
Dial-in conferencing publishing rule |
|
Reverse proxy |
meet.contoso.com |
N/A |
Public |
Server |
Online meeting publishing rule |
|
Next hop pool |
fe01.contoso.net |
sip.contoso.com sip.fabrikam.com pool01.contoso.net csweb.contoso.net |
Internal |
Server |
Front End 01 in Pool01 Default Web site on Front End 01 |
|
Next hop pool |
fe02.contoso.net |
sip.contoso.com sip.fabrikam.com pool01.contoso.net csweb.contoso.net |
Internal |
Server |
Front End 02 in Pool01 Default Web site on Front End 01 |
 Port Summary
Port Summary
The Communications Server 2010 Edge functionality described in this reference architecture is very similar to what was first introduced in Office Communications Server 2007 R2, with the following exceptions:
- Port 80 from the Internet to the reverse proxy external
interface
- Port 8080 from the reverse proxy internal interface to the pool
VIP
- Port 443 from the reverse proxy internal interface to the pool
VIP has changed to port 4443
- Port 4443 from the pool front end(s) to the Edge internal
interface
- If DNS load balancing is deployed, all traffic now goes to each
Edge server (external and internal interfaces) instead of being
split between a hardware load balancer VIP and the Edge server
interfaces
There are several options for the 50,000 – 59,999 port ranges, but the following figure shows the common configuration for interoperability with previous version of Office Communications Server. For details about the options for configuring this port range, see "A/V Edge Service Port Range (50,000 – 59,999) Requirements" in Determining Firewall and 50k Port Range Requirements.

Firewall Details for Single/Scaled Consolidated Edge with DNS Load Balancing: External Interface
| Protocol/port | Used for |
|---|---|
|
HTTP 80 (out) |
Downloading certificate revocation lists |
|
DNS 53 (out) |
External DNS queries |
|
SIP/TLS/443 (in) |
Client to server SIP traffic for remote user access |
|
SIP/MTLS/5061 (in/out) |
Federation |
|
PSOM/TLS/443 (in) |
Remote user access to web conferences for anonymous and federated users |
|
RTP/TCP/50K range (in) |
Media exchange (see "A/V Edge Service Port Range (50,000 – 59,999) Requirements" in Determining Firewall and 50k Port Range Requirements) Required for Office Communications Server 2007 R2 interop |
|
RTP/TCP/50K range (out) |
Media exchange (see "A/V Edge Service Port Range (50,000 – 59,999) Requirements" in Determining Firewall and 50k Port Range Requirements) Required for Office Communications Server 2007 R2 interop Required for Office Communications Server 2007 R2 desktop sharing and federation Required for Communications Server 2010 application sharing, file transfer, or A/V with Windows Live Messenger |
|
RTP/UDP/50K range (in) |
Media exchange (see "A/V Edge Service Port Range (50,000 – 59,999) Requirements" in Determining Firewall and 50k Port Range Requirements) |
|
RTP/UDP/50K range (out) |
Media exchange (see "A/V Edge Service Port Range (50,000 – 59,999) Requirements" in Determining Firewall and 50k Port Range Requirements) |
|
STUN/UDP/3478 (in/out) |
External user access to A/V sessions (UDP) |
|
STUN/TCP/443 (in) |
External user access to A/V sessions and media (TCP) |
Firewall Details for Single/Scaled Consolidated Edge with DNS Load Balancing: Internal Interface
| Protocol/port | Used for |
|---|---|
|
SIP/MTLS/5061 (in/out) |
Federation |
|
PSOM/MTLS/8057 (out) |
Web conferencing traffic; pool to Edge |
|
SIP/MTLS/5062 (out) |
Authentication of A/V users (media authentication service) |
|
STUN/UDP/3478 (out) |
Preferred path for media transfer between internal and external users (UDP) |
|
STUN/TCP/443 (out) |
Alternate path for media transfer between internal and external users (TCP) |
|
HTTP 4443 (out) |
Pushing Central Management database database updates to Edge nodes |
When reading the previous tables, (in) refers to traffic going from a less trusted network to a more trusted network, such as Internet-to-perimeter or perimeter-to-corporate). For example, traffic from the Internet to the Edge external interface or from the Edge internal interface to the next hop pool. (out) refers to traffic going from a more trusted network to a less trusted network, such as corporate-to-perimeter or perimeter-to-Internet). For example, traffic from a corporate pool to the Edge internal interface or from the Edge external interface to the Internet. And, (in/out) refers to traffic that is going both directions.
It is recommended that you only open the ports required to support the functionality for which you are providing external access.
For remote access to work for any edge service, it is mandatory that SIP traffic is allowed to flow bi-directionally as shown in the Single Consolidated Edge figure. Stated another way, the Access Edge service is involved in IM, presence, Web conferencing, and audio/video.
Firewall Details for Reverse Proxy Server: External Interface
| Protocol/port | Use for |
|---|---|
|
HTTP 80 (in) |
External user access to web conferences |
|
HTTPS 443 (in) |
Address book downloads, address book Web query service, client updates, meeting content, device updates, group expansion, dial-in conferencing and online meetings. |
Firewall Details for Reverse Proxy Server: Internal Interface
| Protocol/port | Used for |
|---|---|
|
HTTP 8080 (in) |
Redirected web conferencing traffic from port 80 externally |
|
HTTPS 4443 (in) |
Redirected traffic from port 443 externally to IIS web sites (Ext) |
 Note: Note: |
|---|
| When reading the previous tables, (in) refers to traffic going from a less trusted network to a more trusted network, such as Internet-to-perimeter or perimeter-to-corporate). For example, traffic from Internet to the reverse proxy external interface or from the reverse proxy internal interface to a Standard Edition pool or a hardware load balancer VIP associated with an Enterprise Edition pool. |
External Ports Settings Required for Scaled Consolidated Edge Topology (DNS Load Balanced): External Interface Node 1
| Edge role | Source IP Address | Source Port | Destination IP Address | Destination Port | Transport | Application | Notes |
|---|---|---|---|---|---|---|---|
|
Access |
10.45.16.10 |
80 |
Any |
Any |
TCP |
HTTP |
|
|
Access |
10.45.16.10 |
53 |
Any |
Any |
UDP |
DNS |
|
|
Web Conferencing |
Any |
Any |
10.45.16.20 |
443 |
TCP |
PSOM (TLS) |
|
|
A/V |
10.45.16.30 |
50,000 – 59,999 |
Any |
Any |
TCP |
RTP |
Required only for desktop sharing and/or federation with partners running Office Communications Server 2007 or Office Communications Server 2007 R2. Also required for application sharing or file transfer with Communications Server 2010 federated users. |
|
A/V |
10.45.16.30 |
50,000 – 59,999 |
Any |
Any |
UDP |
RTP |
Required only for federation with partners still running Office Communications Server 2007. |
|
A/V |
Any |
Any |
10.45.16.30 |
50,000 – 59,999 |
TCP |
RTP |
Required only for federation with partners still running Office Communications Server 2007. |
|
A/V |
Any |
Any |
10.45.16.30 |
50,000 – 59,999 |
UDP |
RTP |
Required only for federation with partners still running Office Communications Server 2007. |
|
A/V |
10.45.16.30 |
3478 |
Any |
Any |
UDP |
STUN |
3478 outbound is used to determine the version of Edge server Communications Server 2010 is communicating with and also for media traffic from Edge server to Edge server. Required for federation with Office Communications Server 2007 R2, and also if multiple Edge pools are deployed within a company. |
|
A/V |
Any |
Any |
10.45.16.30 |
3478 |
UDP |
STUN |
|
|
A/V |
Any |
Any |
10.45.16.30 |
443 |
TCP |
STUN |
External Ports Settings Required for Scaled Consolidated Edge Topology (DNS Load Balanced): External Interface Node 2
| Edge role | Source IP Address | Source Port | Destination IP Address | Destination Port | Transport | Application | Notes |
|---|---|---|---|---|---|---|---|
|
Access |
10.45.16.11 |
80 |
Any |
Any |
TCP |
HTTP |
|
|
Access |
10.45.16.11 |
53 |
Any |
Any |
UDP |
DNS |
|
|
Web Conferencing |
Any |
Any |
10.45.16.21 |
443 |
TCP |
PSOM (TLS) |
|
|
A/V |
10.45.16.31 |
50,000 – 59,999 |
Any |
Any |
TCP |
RTP |
Required only for desktop sharing and/or federation with partners running Office Communications Server 2007 or Office Communications Server 2007 R2. Also required for application sharing or file transfer with Communications Server 2010 federated users. |
|
A/V |
10.45.16.31 |
50,000 – 59,999 |
Any |
Any |
UDP |
RTP |
Required only for federation with partners still running Office Communications Server 2007. |
|
A/V |
Any |
Any |
10.45.16.31 |
50,000 – 59,999 |
TCP |
RTP |
Required only for federation with partners still running Office Communications Server 2007. |
|
A/V |
Any |
Any |
10.45.16.31 |
50,000 – 59,999 |
UDP |
RTP |
Required only for federation with partners still running Office Communications Server 2007. |
|
A/V |
10.45.16.31 |
3478 |
Any |
Any |
UDP |
STUN |
3478 outbound is used to determine the version of Edge server Communications Server 2010 is communicating with and also for media traffic from Edge server to Edge server. Required for federation with Office Communications Server 2007 R2, and also if multiple Edge pools are deployed within a company. |
|
A/V |
Any |
Any |
10.45.16.31 |
3478 |
UDP |
STUN |
|
|
A/V |
Any |
Any |
10.45.16.31 |
443 |
TCP |
STUN |
External Ports Settings Required for Scaled Consolidated Edge Topology (DNS Load Balanced): Reverse Proxy
| Edge role | Source IP Address | Source Port | Destination IP Address | Destination Port | Transport | Application | Notes |
|---|---|---|---|---|---|---|---|
|
Reverse Proxy: N/A |
Any |
Any |
10.45.16.40 |
80 |
TCP |
HTTPS |
|
|
Reverse Proxy: N/A |
Any |
Any |
10.45.16.40 |
443 |
TCP |
HTTPS |
Internal Firewall Ports Settings Required for Scaled Consolidated Edge Topology (DNS Load Balanced): Internal Interface Node 1
| Edge role | Source IP Address | Source Port | Destination IP Address | Destination Port | Transport | Application | Notes |
|---|---|---|---|---|---|---|---|
|
Access |
172.25.33.10 |
5061 |
192.168.10.90 192.168.10.91 |
Any |
TCP |
SIP (MTLS) |
Destination will be the Next Hop server(s). In the case of the reference architecture, it is the IP addresses of the two pool front ends. |
|
Access |
192.168.10.90 192.168.10.91 |
Any |
172.25.33.10 |
5061 |
TCP |
SIP (MTLS) |
Source will be the Next Hop server(s). In the case of the reference architecture, it is the IP addresses of the two pool front ends. |
|
Web Conferencing |
Any |
Any |
172.25.33.10 |
8057 |
TCP |
PSOM (MTLS) |
|
|
A/V |
192.168.10.90 192.168.10.91 |
Any |
172.25.33.10 |
5062 |
TCP |
SIP (MTLS) |
Include all front end servers using this particular A/V authentication service. |
|
A/V |
Any |
Any |
172.25.33.10 |
3478 |
UDP |
STUN |
|
|
A/V |
Any |
Any |
172.25.33.10 |
443 |
TCP |
STUN |
|
|
A/V |
192.168.10.90 192.168.10.91 |
Any |
172.25.33.10 |
4443 |
TCP |
HTTPS |
Used for the Central Management database database replication, include all front end servers. |
Internal Firewall Ports Settings Required for Scaled Consolidated Edge Topology (DNS Load Balanced): Internal Interface Node 2
| Edge role | Source IP Address | Source Port | Destination IP Address | Destination Port | Transport | Application | Notes |
|---|---|---|---|---|---|---|---|
|
Access |
172.25.33.11 |
5061 |
192.168.10.90 192.168.10.91 |
Any |
TCP |
SIP (MTLS) |
Destination will be the Next Hop server(s). In the case of the reference architecture, it is the IP addresses of the two pool front ends. |
|
Access |
192.168.10.90 192.168.10.91 |
Any |
172.25.33.11 |
5061 |
TCP |
SIP (MTLS) |
Source will be the Next Hop server(s). In the case of the reference architecture, it is the IP addresses of the two pool front ends. |
|
Web Conferencing |
Any |
Any |
172.25.33.11 |
8057 |
TCP |
PSOM (MTLS) |
|
|
A/V |
192.168.10.90 192.168.10.91 |
Any |
172.25.33.11 |
5062 |
TCP |
SIP (MTLS) |
Include all front end servers using this particular A/V authentication service. |
|
A/V |
Any |
Any |
172.25.33.11 |
3478 |
UDP |
STUN |
|
|
A/V |
Any |
Any |
172.25.33.11 |
443 |
TCP |
STUN |
|
|
A/V |
192.168.10.90 192.168.10.91 |
Any |
172.25.33.11 |
4443 |
TCP |
HTTPS |
Used for the Central Management database database replication, include all front end servers. |
Internal Firewall Ports Settings Required for Scaled Consolidated Edge Topology (DNS Load Balanced): Reverse Proxy
| Edge role | Source IP Address | Source Port | Destination IP Address | Destination Port | Transport | Application |
|---|---|---|---|---|---|---|
|
Reverse proxy: N/A |
172.25.33.40 |
Any |
192.168.10.190 |
8080 |
TCP |
HTTPS |
|
Reverse proxy: N/A |
172.25.33.40 |
Any |
192.168.10.190 |
4443 |
TCP |
HTTPS |
 DNS Summary
DNS Summary
DNS record requirements for remote access to Communications Server are fairly straightforward compared to those for certificates and ports. Also, many records are optional, depending on how you configure Communicator clients and whether you enable federation.
For details on Communications Server 2010 DNS requirements, see “Required DNS Records for Edge Components” in Communications Server 2010 Help.
For details on configuring automatic configuration of Microsoft Communicator "14" clients if split-brain DNS is not configured, see “Automatic Configuration without Split Brain DNS”.
The following table contains a summary of the DNS records that are required to support the single consolidated edge topology shown in the Single Consolidated Edge Topology figure. Note that certain DNS records are required only for Communicator client automatic configuration. If you plan to use GPOs to configure Communicator clients, the associated records are not necessary.
 Important: Important: |
|---|
| Edge/Reverse Proxy Network Adapter Requirements To avoid routing issues be sure there are at least two network adapters in your edge and reverse proxy servers and that the default gateway is set only on the network adapter associated with the external interface. For example, as shown in Scaled Consolidated Edge Topology figure reference architecture, the default gateway would point to the external firewall (10.45.16.1). You can configure two network adapters in your Edge server as follows:
|
DNS Records Required for Scaled Consolidated Edge Topology (DNS Load Balanced): Consolidated Edge
| Location | Type | FQDN | IP Address | Port | Maps to/comments |
|---|---|---|---|---|---|
|
External DNS |
A |
access.contoso.com |
63.123.155.10/24 |
Access Edge external interface (contoso) (NODE 1) |
|
|
External DNS |
A |
access.contoso.com |
63.123.155.11/24 |
Access Edge external interface (contoso) (NODE 2) |
|
|
External DNS |
A |
access.fabrikam.com |
63.123.155.10/24 |
Access Edge external interface (fabrikam) (NODE 1) |
|
|
External DNS |
A |
access.fabrikam.com |
63.123.155.11/24 |
Access Edge external interface (fabrikam) (NODE 2) |
|
|
External DNS |
A |
webcon.contoso.com |
63.123.155.20/24 |
Web Conferencing Edge external interface (NODE 1) |
|
|
External DNS |
A |
webcon.contoso.com |
63.123.155.21/24 |
Web Conferencing Edge external interface (NODE 2) |
|
|
External DNS |
A |
av.contoso.com |
63.123.155.30/24 |
A/V Edge external interface (NODE 1) |
|
|
External DNS |
A |
av.contoso.com |
63.123.155.31/24 |
A/V Edge external interface (NODE 2) |
|
|
External DNS |
SRV |
_sip._tls.contoso.com |
access.contoso.com |
443 |
Access Edge external interface (access.contoso.com) Required for Office Communicator automatic configuration to work externally |
|
External DNS |
SRV |
_sip._tls.fabrikam.com |
access.fabrikam.com |
443 |
Access Edge external interface (access.contoso.com) Required for Office Communicator automatic configuration to work externally. |
|
External DNS |
SRV |
_sipfederationtls._tcp.contoso.com |
access.contoso.com |
5061 |
Access Edge external interface (access.contoso.com) Required for enhanced federation. |
|
External DNS |
SRV |
_sipfederationtls._tcp.fabrikam.com |
access.fabrikam.com |
5061 |
|
|
Internal DNS |
A |
csedge.contoso.net |
172.25.33.10/24 |
Consolidated Edge internal interface (DNS load balancer) |
|
|
Internal DNS |
A |
csedge.contoso.net |
172.25.33.11/24 |
Consolidated Edge internal interface (DNS load balancer) |
|
|
Internal DNS |
A |
con01.contoso.net |
172.25.33.10/24 |
Consolidated Edge internal interface (NODE 1) |
|
|
Internal DNS |
A |
con01.contoso.net |
172.25.33.11/24 |
Consolidated Edge internal interface (NODE 2) |
DNS Records Required for Scaled Consolidated Edge Topology (DNS Load Balanced): Reverse Proxy
| Location | Type | FQDN | IP Address | Port | Maps to/comments |
|---|---|---|---|---|---|
|
External DNS |
A |
ocsrp.contoso.com |
63.123.155.40/24 |
Used to publish Address Book Service, group expansion, and Online Meeting content. |
|
|
External DNS |
A |
dialin.contoso.com |
63.123.155.40/24 |
Dial-in conferencing published externally |
|
|
External DNS |
A |
meet.contoso.com |
63.123.155.40/24 |
Online Meetings published externally |
|
|
External DNS |
A |
csweb-ext.contoso.com |
63.123.155.40/24 |
Communications Server 2010 external web farm FQDN |
|
|
Internal DNS |
A |
rproxy.contoso.com |
172.25.33.40/24 |
Reverse proxy internal interface |
DNS Records Required for Scaled Consolidated Edge Topology (DNS Load Balanced): Next Hop Pool
| Location | Type | FQDN | IP Address | Port | Maps to/comments |
|---|---|---|---|---|---|
|
Internal DNS |
A |
pool01.contoso.net |
192.168.10.90/24 |
Pool01 (DNS LB) |
|
|
Internal DNS |
A |
pool01.contoso.net |
192.168.10.91/24 |
Pool01 (DNS LB) |
|
|
Internal DNS |
A |
fe01.contoso.net |
192.168.10.90/24 |
Pool01 front end server (NODE 1) |
|
|
Internal DNS |
A |
fe02.contoso.net |
192.168.10.91/24 |
Pool01 front end server (NODE 2) |
|
|
Internal DNS |
A |
csweb.contoso.net |
192.168.10.190/24 |
Pool01 (VIP) for client to server web traffic |
|
|
Internal DNS |
A |
sql01.contoso.net |
192.168.10.100/24 |
Pool01 backend Microsoft SQL Server 2005/ Microsoft SQL Server 2008 database server |
|
|
Internal DNS |
A |
pool01.contoso.com |
192.168.10.90/24 |
Pool01 (DNS LB) – for Communicator automatic configuration to work internally |
|
|
Internal DNS |
A |
pool01.fabrikam.com |
192.168.10.90/24 |
Pool01 (DNS LB) – for Communicator automatic configuration to work internally |
|
|
Internal DNS |
A |
sip.contoso.com |
192.168.10.90/24 |
Required for Communicator automatic configuration to work internally |
|
|
Internal DNS |
A |
sip.fabrikam.com |
192.168.10.90/24 |
Required for Communicator automatic configuration to work internally |
|
|
Internal DNS |
A |
dialin.contoso.com |
192.168.10.190/24 |
Dial-in conferencing published internally |
|
|
Internal DNS |
A |
meet.contoso.com |
192.168.10.190/24 |
Online Meetings published internally |
|
|
Internal DNS |
A |
admin.contoso.com |
192.168.10.190/24 |
Admin UI published internally |
|
|
Internal DNS |
SRV |
_sipinternaltls._tcp.contoso.com |
pool01.contoso.com |
5061 |
Required for Communicator automatic configuration to work internally |
|
Internal DNS |
SRV |
_sipinternaltls._tcp.fabrikam.com |
pool01.fabrikam.com |
5061 |
Required for Communicator automatic configuration to work internally |
|
Internal DNS |
SRV |
_ntp._udp.contoso.com |
timeServerFQDN |
123 |
NTP source required for Phone Edition devices |
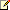 Note: Note: |
|---|
| VIP = virtual IP address |
 Important: Important: |
|---|
| The records listed in the previous table are shown with either a .net extension or a .com extension to highlight which zone they need to reside in if split-brain DNS is not in use. If you are using split-brain DNS, all records would be in the same zone, with the only distinction being whether they are in the internal or external version. For details, see “Split-Brain DNS”. |

