Outbreak Protection (OP) is a revolutionary real time anti-spam, anti-virus, and anti-phishing technology capable of proactively protecting an MDaemon email infrastructure automatically and within minutes of an outbreak. Included in SecurityPlus for MDaemon, Outbreak Protection requires SecurityPlus for MDaemon 3.0 or later and MDaemon PRO 9.5 or later, and it is accessible from MDaemon's Security menu (Security » Outbreak protection..., or Ctrl+Shift+1).
Outbreak Protection is completely content agnostic, meaning that it doesn't rely on strict lexical analysis of message content. Thus, it doesn't require heuristic rules, content filtering, or signature updates. Further, that means it is not fooled by the addition of seed text, clever spelling changes, social engineering tactics, language barriers, or differences in encoding techniques. Instead, OP relies on the mathematical analysis of message structure and message distribution characteristics over SMTPit analyzes "patterns" associated with an email transmission and compares them to similar patterns collected from millions of email messages worldwide, which are sampled and compared in real time.
Because messages are being analyzed worldwide in real time, protection is provided within minutesoften secondsof a new outbreak. For viruses, this level of protection is critical since it is often hours after an outbreak before a traditional antivirus vendor can verify and submit a virus signature update, and it can then be even longer before that update is put into production use. During that interval, servers without Outbreak Protection are vulnerable to that particular outbreak. Similarly, for spam messages it will often take time and effort to analyze the spam and create a safe filtering rule before it will be recognized by traditional heuristic and content based systems.
It is important to note, however, that the Outbreak Protection feature in SecurityPlus is not a replacement for traditional anti-virus, anti-spam, and anti-phishing techniques. In fact, OP provides another specialized layer of protection on top of the existing heuristics, signature, and content based tools found within SecurityPlus and MDaemon. Specifically, OP is designed to deal with large-scale outbreaks rather than old, unique, or specifically targeted messages that can be more readily caught by the traditional tools.
|
|
Outbreak Protection is based on CommTouch RPD and Zero-Hour technology. It works by extracting patterns from your incoming mail and comparing them to patterns taken from millions of internet email messages sampled daily from numerous sources all over the world. In no way is the actual content of any message ever transmitted, nor can the message content ever be derived from the extracted patterns. |
For more on SecurityPlus and Outbreak Protection, see the remainder of this section and visit: www.altn.com.
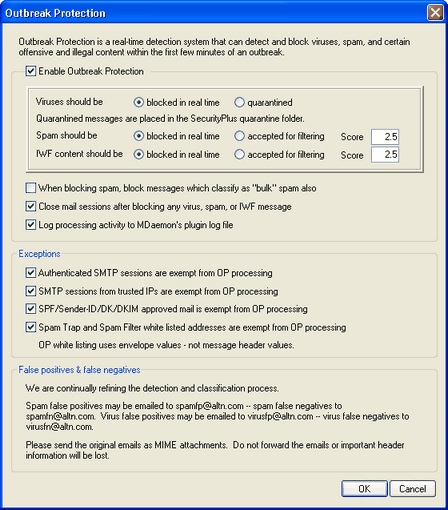
Outbreak Protection
Enable Outbreak Protection
Click this checkbox to enable Outbreak Protection for your server. Incoming messages will be analyzed to see if they are part of an ongoing virus, spam, or phishing outbreak. The remaining options on this dialog are used to determine what will be done with messages found to be part of an outbreak, and to designate the senders that will be exempt from OP processing.
Viruses should be...
blocked in real time
Select this option if you wish to block messages during the SMTP process when they are determined to be part of a virus outbreak. These messages will not be quarantined or delivered to their intended recipientsthey will be rejected by the server.
quarantined
Select this option if you wish to accept messages that OP determines are part of a virus outbreak. Although these messages will not be rejected by the server, they will be quarantined instead of delivered to their intended recipients. Quarantined messages are placed in SecurityPlus' quarantine folder.
Spam should be...
blocked in real time
Select this option if you wish to block messages during the SMTP process when OP confirms that they are part of a spam outbreak. These messages will not be flagged as spam and delivered to their intended recipientsthey will be rejected by the server. Messages classified by OP as "bulk" mail will not be blocked by this option unless you activate the When blocking spam, block messages which classify as "bulk" spam also option below. Messages classified as "bulk" by OP could simply be a part of certain very large mailing lists or other similar widely distributed content, so you may or may not consider those types of messages to be spam. For that reason, those types of messages generally shouldn't be scored negatively or blocked by OP.
accepted for filtering
Select this option if you wish to accept messages that OP confirms to be part of a spam outbreak, so that they can then be subjected to spam filtering and content filter processing. These messages will not be blocked by OP, but they will have their Spam Filter scores adjusted according to the Score option below.
|
|
When using the accepted for filtering option, OP will not directly cause a confirmed spam message to be blocked, but a message may still be blocked by MDaemon during the SMTP process if you have configured the Spam Filter to use the SMTP rejects messages with scores greater than or equal to [xx] option, located on the Spam Filter screen. For example, if the scoring option below caused a messages Spam Filter score to be 15.0, then the message would still be rejected as spam if you had also configured the Spam Filters SMTP rejects... option to reject messages that have a score of 15.0 or greater. |
Score
When using the accepted for filtering option above, this amount will be added to a messages Spam Filter score when OP confirms that the message is part of a spam outbreak.
IWF Content
The following option applies to content identified by the Internet Watch Foundation (IWF) as referring to child abuse image sites (i.e. child pornography sites). It enables OP to use an integrated URL list provided by the IWF to detect and tag messages that refer to that content. The IWF operates an independent internet hotline for reporting potentially illegal online content, including child abuse content hosted anywhere in the world. They work in partnership with the police, governments, the wider online industry and the public to combat the availability of illegal online content. The Foundations URL list is updated daily with new sites hosting child abuse images.
Many organizations have internal compliance rules governing the content of email sent or received by its employees, especially with regard to obscene or illegal material. In addition, many countries have outlawed the sending or receipt of such content. This feature can assist in your efforts to ensure compliance.
For more on the IWF, see:
IWF content should be...
blocked in real time
Choose this option if you wish to reject incoming messages during the SMTP process when they have IWF restricted content.
accepted for filtering
Choose this option if you wish to increase a messages Spam Filter score instead of rejecting it when it has IWF restricted content. The Spam Filter score will be increased by the amount specified in the Score option below.
Score
When the accepted for filtering option above is selected, this is the amount that will be added to a messages Spam Filter score when it contains IWF restricted content.
When blocking spam, block messages which classify as bulk spam also
Sometimes OP will identify certain messages that could be considered spam but aren't being sent from a known spammer or bot-netas is sometimes the case with legitimate bulk mailings and newsletters. OP classifies these types of messages as "Spam (bulk)" rather than "Spam (confirmed)." Click this checkbox if you wish to apply OPs spam blocking features to "Spam (bulk)" mail as well. If this option is disabled, only messages classified as "Spam (confirmed)" will be affected by OPs spam blocking features above. Accepting this type of spam for later processing may be necessary for sites that want to receive bulk mailings but for some reason cannot white list the source or recipient.
Log processing activity to MDaemon's plugin log file
Enable this checkbox if you wish to log all OP processing activity into MDaemon's plugin log file.
Exceptions
Authenticated SMTP sessions are exempt from OP processing
When this option is enabled, authenticated SMTP sessions are exempt from OP processing. This means that messages sent during that session will not be subjected to Outbreak Protection checks.
SMTP sessions from trusted IPs are exempt from OP processing
Enable this option if you wish to exempt trusted IP addresses from Outbreak Protectionmessages arriving from a server at a trusted IP address not be subjected to OP checks.
SPF/Sender-ID/DK/DKIM approved mail is exempt from OP processing
Click this checkbox if you wish to exempt a message from OP processing when the sending domain appears on the Approved List and it is validated by SPF, Sender-ID, DK, or DKIM.
Spam Trap and Spam Filter white listed addresses are exempt from OP processing
Click this option if you wish to exempt the Spam Honeypots and Spam Filter white lists from Outbreak Protection. The "White List" applies to the recipient, or RCPT value given during the SMTP session. The "White List (from)" applies to the sender, or MAIL value given during the SMTP session. These operations are not based on message header values.
False Positives and False Negatives
False positives, or classifying a legitimate message improperly as part of an outbreak, should rarely if ever happen. Should a false positive occur, however, you can send that message to us at spamfp@altn.com for spam/phishing false positives or virusfp@altn.com for virus false positives, so that we can use it to help refine and improve our detection and classification processes.
False negatives, or classifying a message as not part of an outbreak even though it is still spam or an attack, will happen more often than false positives. However, it worth noting that OP is not designed to catch all spam, virus attacks, and the likeit is simply one layer of protection that specifically targets outbreaks. Old messages, specifically targeted messages and the like, which are not part of a currently ongoing outbreak, might pass the OP check. Those sorts of messages should then be caught by the other SecurityPlus and MDaemon features further down the processing chain. Should a false negative occur, however, you can send that message to us at spamfn@altn.com for spam/phishing false negatives or virusfn@altn.com for virus false negatives, so that we can use it to help refine and improve our detection and classification processes.
When sending improperly classified messages to us, the original email should be sent as a MIME email attachment rather than forwarded. Otherwise, headers and other information critical to the classification process will be lost.